Encrypted Traffic Analysis
Unlock encrypted threats with GREYCORTEX Mendel
Whether your network traffic is encrypted or not, GREYCORTEX Mendel ensures you achieve comprehensive security by combining advanced detection techniques. These include behavioral modeling with machine learning, statistical methods, fingerprinting, threat intelligence, and deep packet inspection for encrypted data. This multifaceted approach effectively enables you to identify hidden channels, vulnerabilities, and advanced cyber threats, providing you robust protection for your network.
Analyzing encrypted traffic with a key
You also have the option to insert a private RSA key, allowing Mendel to decrypt network communication and giving you access to its full detection capabilities, including deep packet inspection. Alternatively, you can use an external decryption tool, such as a firewall, ADC or SSL Orchestrator, to send a copy of your decrypted network traffic to Mendel, enabling you to analyze your traffic without limitations.
Using Mendel, you can:
- - Flag suspicious behavior, indicating potential cyber threats or insider risks.
- - Identify repetitive patterns, revealing APTs, unknown malware, or C&C.
- - Analyze your SSL/TLS data to detect connections with blacklisted IPs or domains.
- - Use JA3 to identify clients in your encrypted traffic.
- - Receive alerts to weak or outdated encryption use.
- - Detect ongoing or completed network scans.
- - Decrypt communications with a RSA key or analyze decrypted traffic from external decryption tools.
Showcases: What You Can Identify in Encrypted Traffic
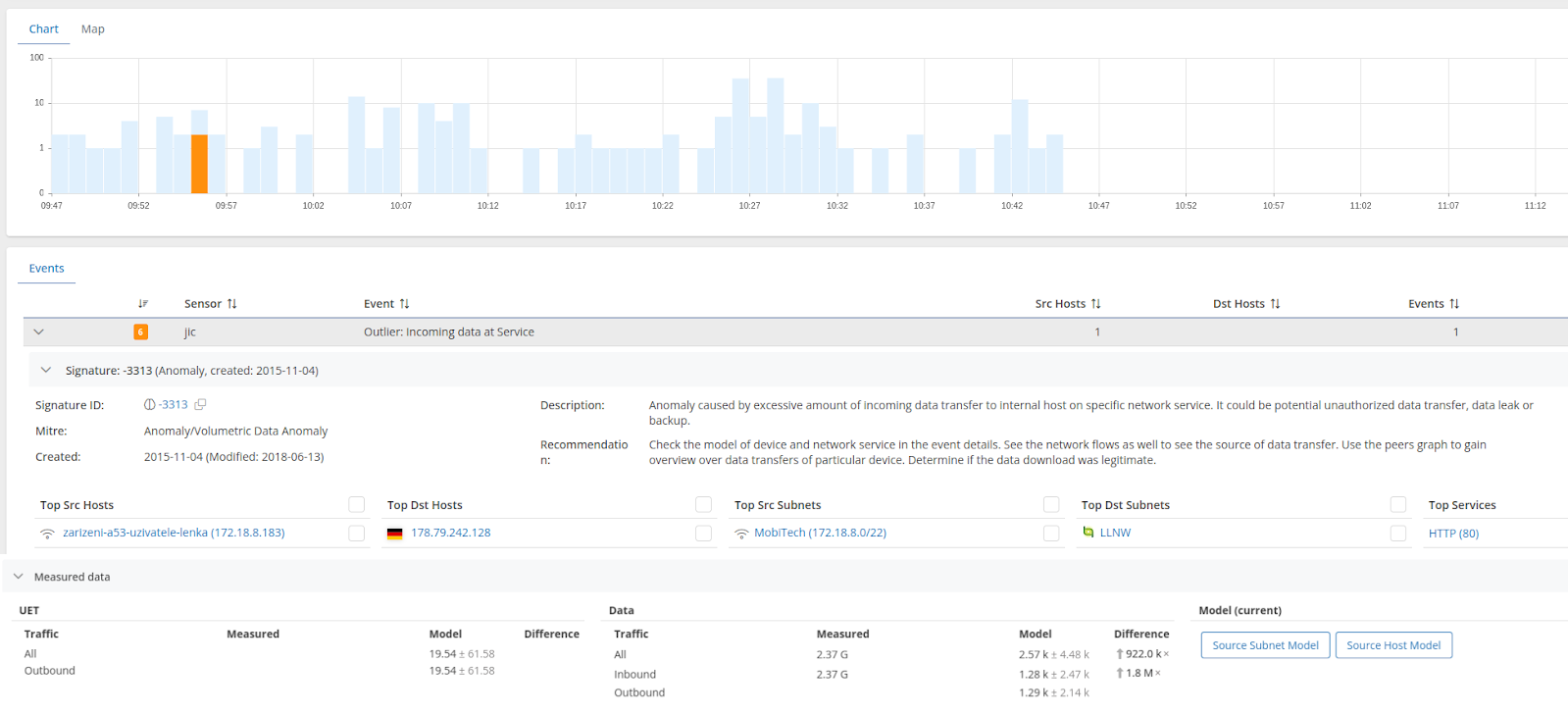
Uncover behavioral outliers
As Mendel enables you to model the behavior of the entire network and individual objects within it, it means you can detect anomalous and malicious outliers even in encrypted traffic. This capability serves to provide you with an indicator of a potential cyberattack, data exfiltration, or insider threat you need to respond quickly.
Detect trojans and C&C
Mendel allows you to detect repetitive communication in encrypted traffic, a common indicator of machine behavior that could signal APTs, unknown malware, or software updates. Employing several detection methods, Mendel lets you evaluate communication repetition over time and report the results, including the standard firewall evasion technique where malware contacts its Command and Control server.
Prevent communication with blacklisted IPs, and domain certificates
Understanding the risks associated with suspicious websites and unverified email attachments is crucial for preventing your network from being exposed to phishing, malware, and congestion. Mendel enables you to identify such threats by analyzing SSL/TLS protocols and the content of the certificates, meaning you can detect any communication with blacklisted IPs or low-reputation senders through its extensive threat Intelligence.
Additionally, Mendel issues you warnings if someone in your network is connecting to a domain with a certificate that is known to be used by cybercriminals or is potentially malicious.
Deploy JA3 fingerprinting
When communication is encrypted, you cannot identify who is connecting to your network. Cybercriminals leverage encryption to conceal their activities, such as Command and Control (C2) channels. Mendel lets you deploy JA3 fingerprinting to allow you to identify connecting clients, including malware, servers, web APIs, or browsers. Consequently, JA3 serves as a valuable Indicator of Compromise, assisting you in your threat hunting.
Identify weak or outdated encryption algorithms
Mendel promptly identifies and alerts you to the use of weak or outdated encryption, which could expose your network to potential security vulnerabilities and data breaches. Moreover, Mendel issues warnings if your encryption certificate is nearing expiration or is no longer valid.
Detect network scans
Cybercriminals conduct network scans to gather insights and identify vulnerabilities for exploitation, aiming to infiltrate, compromise, and escalate privileges. Mendel enables you to prevent unauthorized intrusion attempts by helping you detect any ongoing or completed network scans.

Get a Thorough Network Security Audit
Over the course of 30 days, Mendel will diligently monitor your network.
At the end of this period, our team of security professionals will provide you with a comprehensive
incident security report detailing critical security issues and offering recommendations
for their resolution.