Reliable Sensitive Data Monitoring
The highest priority of any IT security department is protecting your company’s sensitive data to maintain your business reputation, customer trust, and compliance with government regulations, thereby avoiding costly fines.
Take control of your sensitive data with GREYCORTEX Mendel
Cyber attackers often rely on familiar tactics to breach your network and steal your valuable data. Having rich threat intelligence with the latest detected threats, as well as the ability to conduct quick network audits and respond promptly in the event of an attack, aids in securing your network against the vast majority of cyber threats. Even in instances where cyber attackers deploy cutting-edge tactics, Mendel’s vigilant detection algorithms are standing by to allow you to effectively spot and prevent the most sophisticated and emerging threats from accessing your network.
Mendel allows you to:
- - Visualize all your devices, including OT and IoT devices.
- - Automatically identify hosts and enable custom rule creation.
- - Rapidly review user behavior, detect malicious patterns, and identify unauthorized user access.
- - Set alerts for breached rules or critical security events.
- - Seamlessly integrate Mendel with your security tools for swift response.
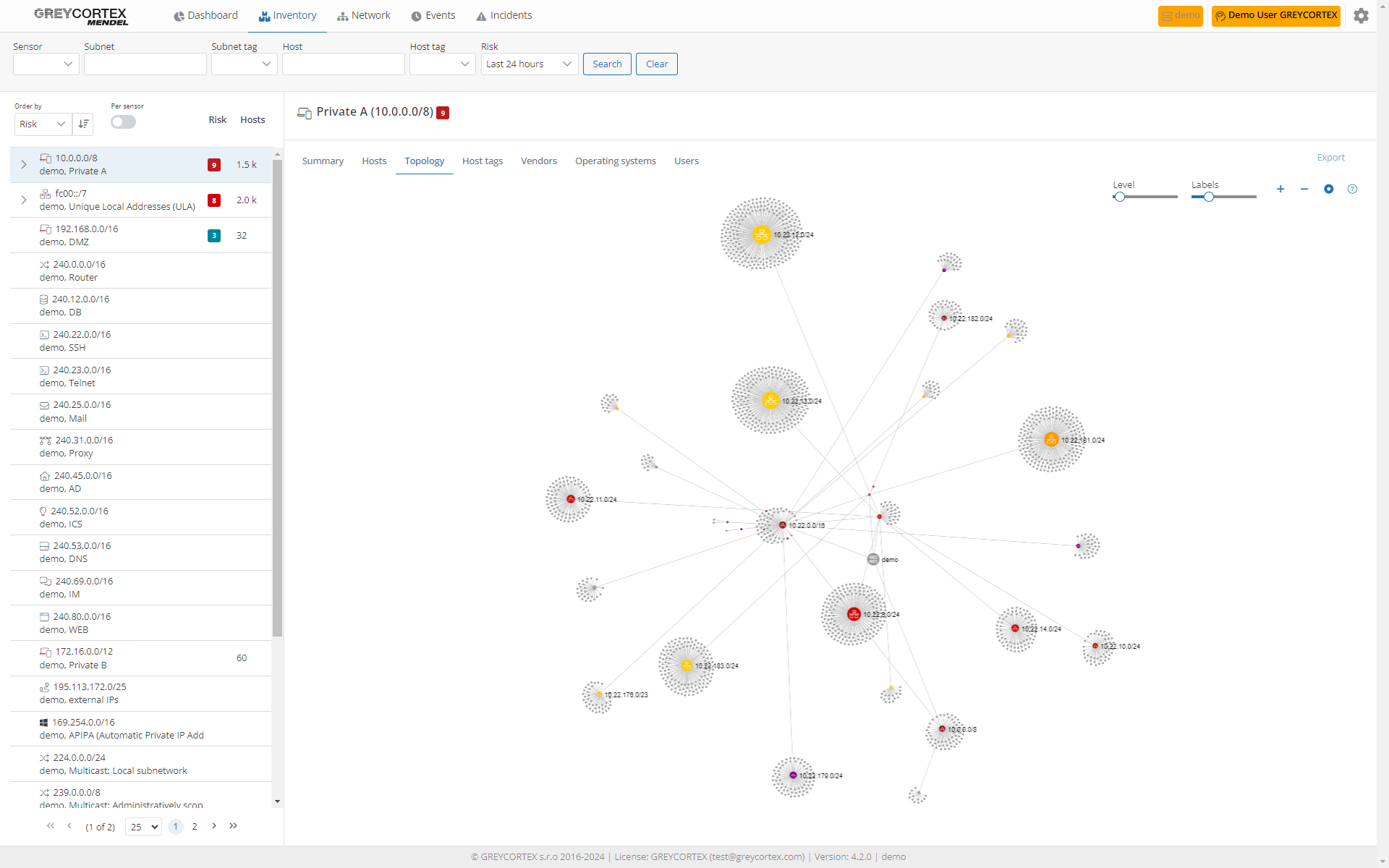
Map Your Entire Network
To safeguard sensitive data, having a deep understanding of your network is crucial. GREYCORTEX Mendel empowers you by delivering real-time visualization of all devices, including IoT devices like personal phones, employee laptops, and OT devices, such as printers or HVAC systems.
Extensive host insights
Using Mendel, you can identify and store data on all communicating network devices. This provides you with a detailed list of all networks, subnetworks, and essential device information such as hostnames, users, tags, and operating systems. You can also visualize connections among devices and users for further detailed inspection.
User identity integration
Mendel can be integrated with user identity data from sources like Active Directory/LDAP or Cisco ISE to connect devices with user names.
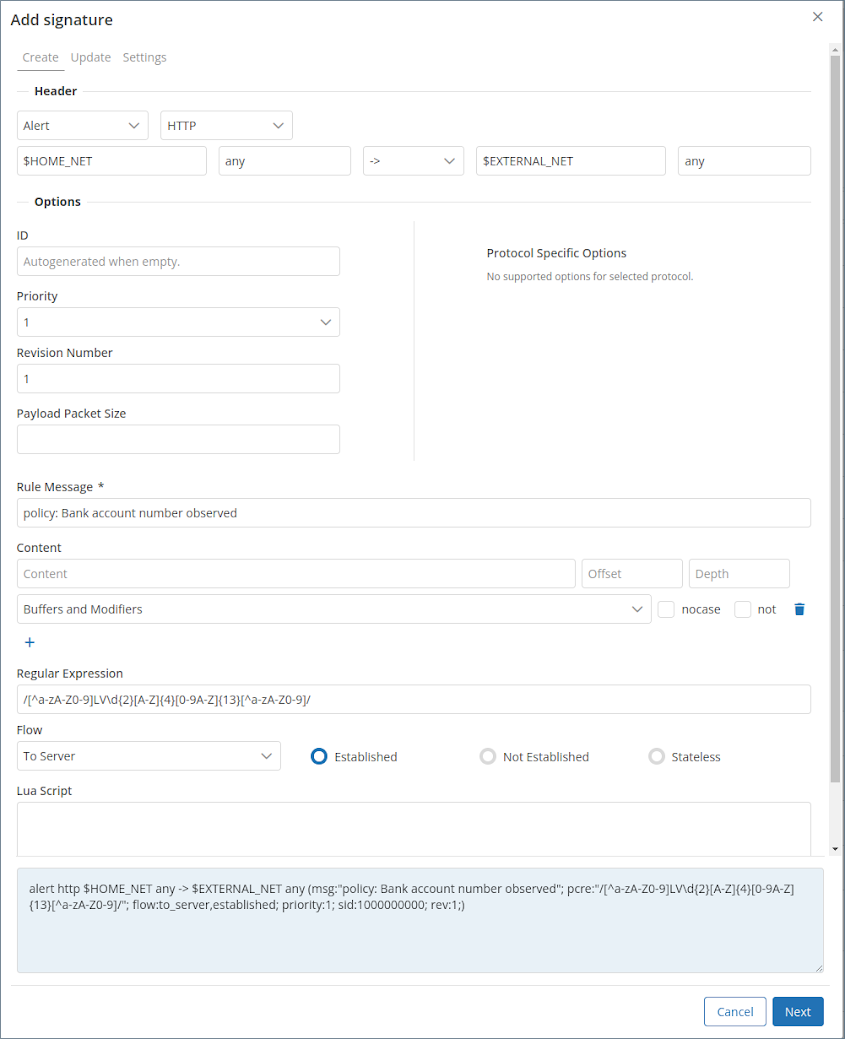
Set Rules to Monitor Data Movement
When you know your network the best, you can inform Mendel about the data critical for your business.
Automatic host identification
Using Mendel, you can automatically identify key data hosts like storage and Active Directory servers. This gives you the ability to ensure these servers’ availability by verifying that the services return data and maintain confidentiality through monitoring for suspicious connections or access. Server identification is carried out using the tagging engine, allowing you to apply filters to gather more information about these servers.
Custom rule creation
These rules enable you to detect the transmission of confidential data based on file name, hash, or content, as well as identify unauthorized access attempts and unusual network behavior. They also help detect and prevent new types of attacks before they become widely known.

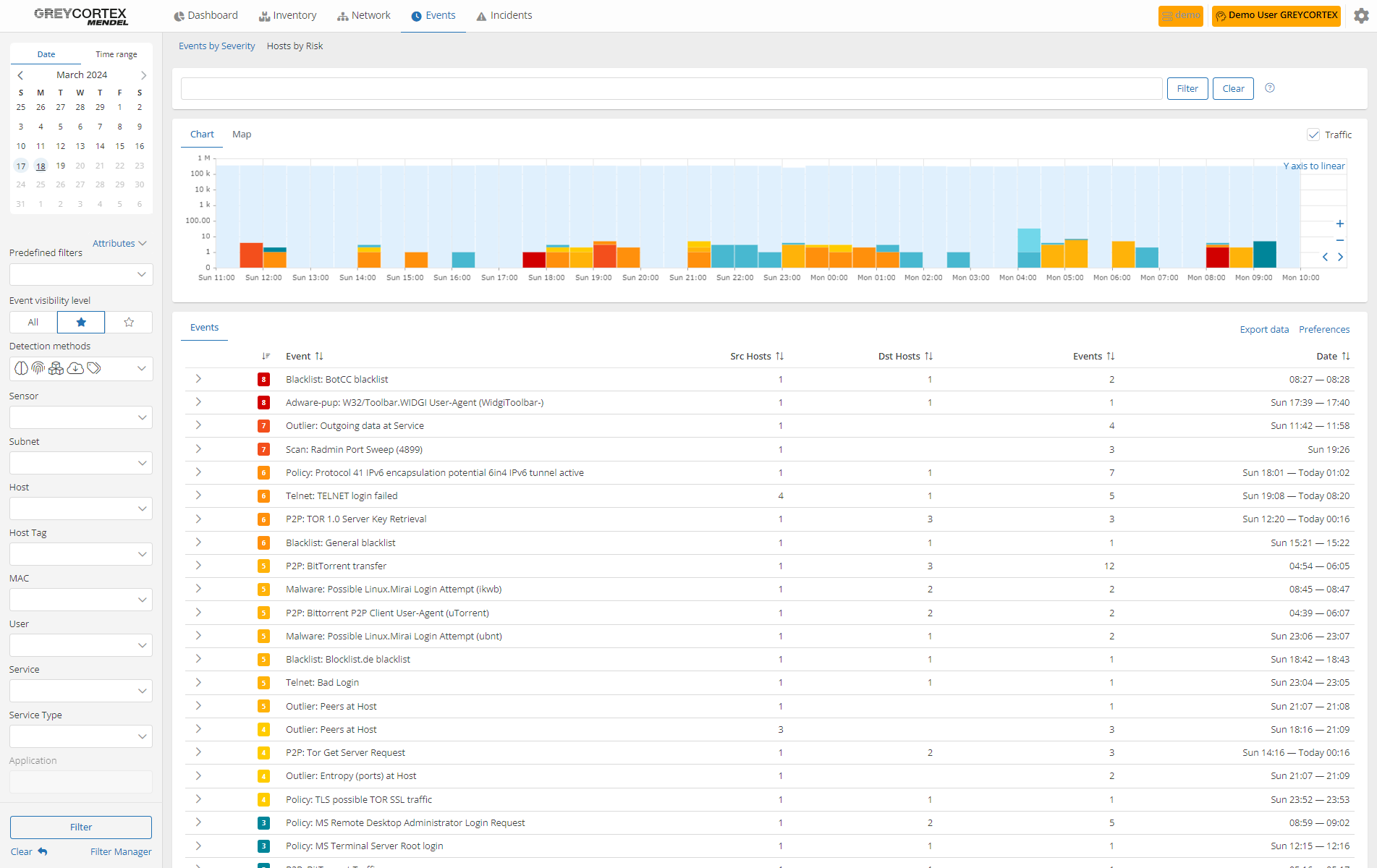
Regularly Audit Your Network
Conducting regular network audits is essential for securing sensitive data. GREYCORTEX Mendel helps you successfully carry out this process with ease.
User behavior analysis
Mendel allows you to quickly review user behavior in your network, identifying improper communications with restricted systems or VPN access under blocked accounts. It also helps you ensure external subcontractors do not retain unnecessary or unauthorized access or privileges.
Malicious pattern detection
Mendel’s learning capabilities enable you to distinguish between normal and suspicious behavior through the identification of malicious patterns, changes, and anomalies, allowing you to effectively detect sophisticated threats.
Security policy validation
Additionally, Mendel also enables you to carry out a quick and easy review of security policy configurations and permissions, ensuring daily compliance.

“When you say GREYCORTEX Mendel, the key word that comes to mind is visibility.
And CD Projekt RED completely supports this statement.”
Get Alerts and React in Real-time
Receiving prompt notifications when a malicious attempt to infiltrate your network or steal data occurs is crucial. Mendel alerts you via email or SMS whenever a set rule is breached or a critical security event occurs, meaning you can act swiftly and prevent attacks from taking hold.
Integration capabilities
Mendel integrates seamlessly with most security solutions, including firewalls, Network Access Control (NAC), and Endpoint Detection and Response (EDR) platforms. This empowers you to halt malicious activities directly within Mendel by isolating the affected devices, enhancing your network’s security response.

Get a Comprehensive Network Security Audit
Over the course of 30 days, Mendel will diligently monitor your network.
At the end of this period, our team of security professionals will provide you with
a comprehensive incident security report detailing critical security issues and
offering recommendations for their resolution.