The NIS2 Directive has introduced a new era of cybersecurity regulation across the EU. Its focus on process setup and technical requirements challenges organizations to rethink how they manage cybersecurity risks. While setting up governance frameworks is crucial, NIS2 also mandates essential technical measures like asset management, network segmentation, and incident detection.
For many organizations, these technical demands can feel overwhelming: How do we meet them effectively? Do we have the right tools in place? This is where GREYCORTEX Mendel steps in, helping you bridge the gap between process and technology. Mendel empowers organizations like yours to simplify compliance by offering you the tool to monitor, secure, and optimize their network infrastructure effectively.
In this article, we’ll show you how Mendel supports compliance with the technical aspects of NIS2, helping you strengthen your cybersecurity posture while meeting the directive’s requirements.
A Brief Overview of the NIS2 Directive
The NIS2 Directive (Network and Information Security) is a pivotal EU cybersecurity regulation introduced in December 2020. Its primary objective is to establish a uniform level of cybersecurity protection across all EU Member States by mandating specific requirements and measures. Compared to its predecessor, the NIS Directive, NIS2 represents a significant expansion of scope and ambition.
While the specific requirements may vary by country as national legislations adopt the directive, certain challenges remain universal. This is where GREYCORTEX Mendel can help. No matter the regulatory nuances in your country, Mendel provides you with practical tools and insights to address key technical requirements, ensuring your organization stays secure and compliant.
NIS2 in Practice: How GREYCORTEX Mendel Helps
Asset management
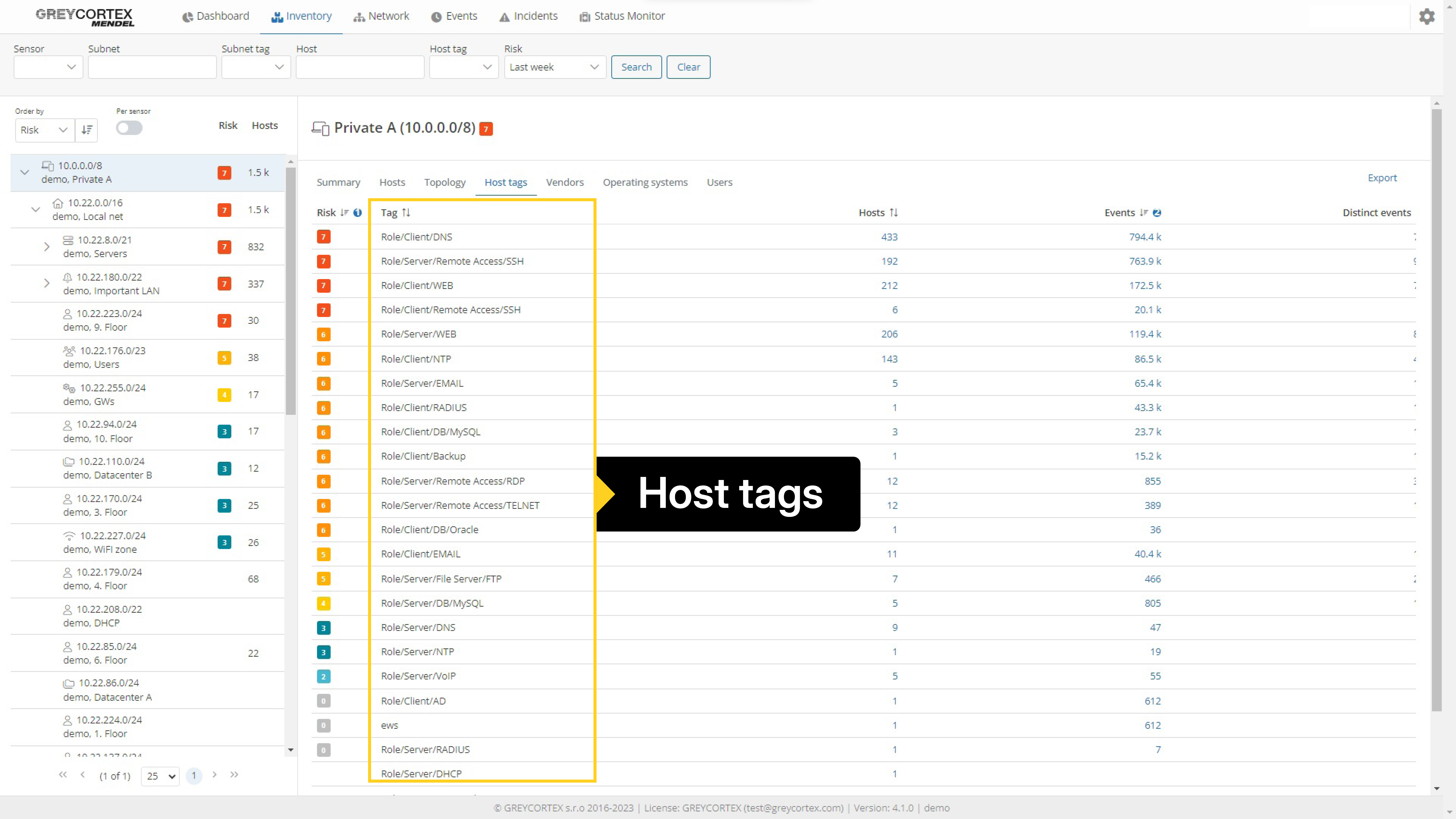
Organizations must maintain visibility of all devices and systems within their infrastructure, including their interactions. GREYCORTEX Mendel lets you simplify this process by automatically auditing assets and mapping their connections.
For instance, a regional healthcare provider discovered 15 undocumented devices using Mendel. This helped them uncover legacy systems that were vulnerable to exploitation and provided a roadmap for mitigation.
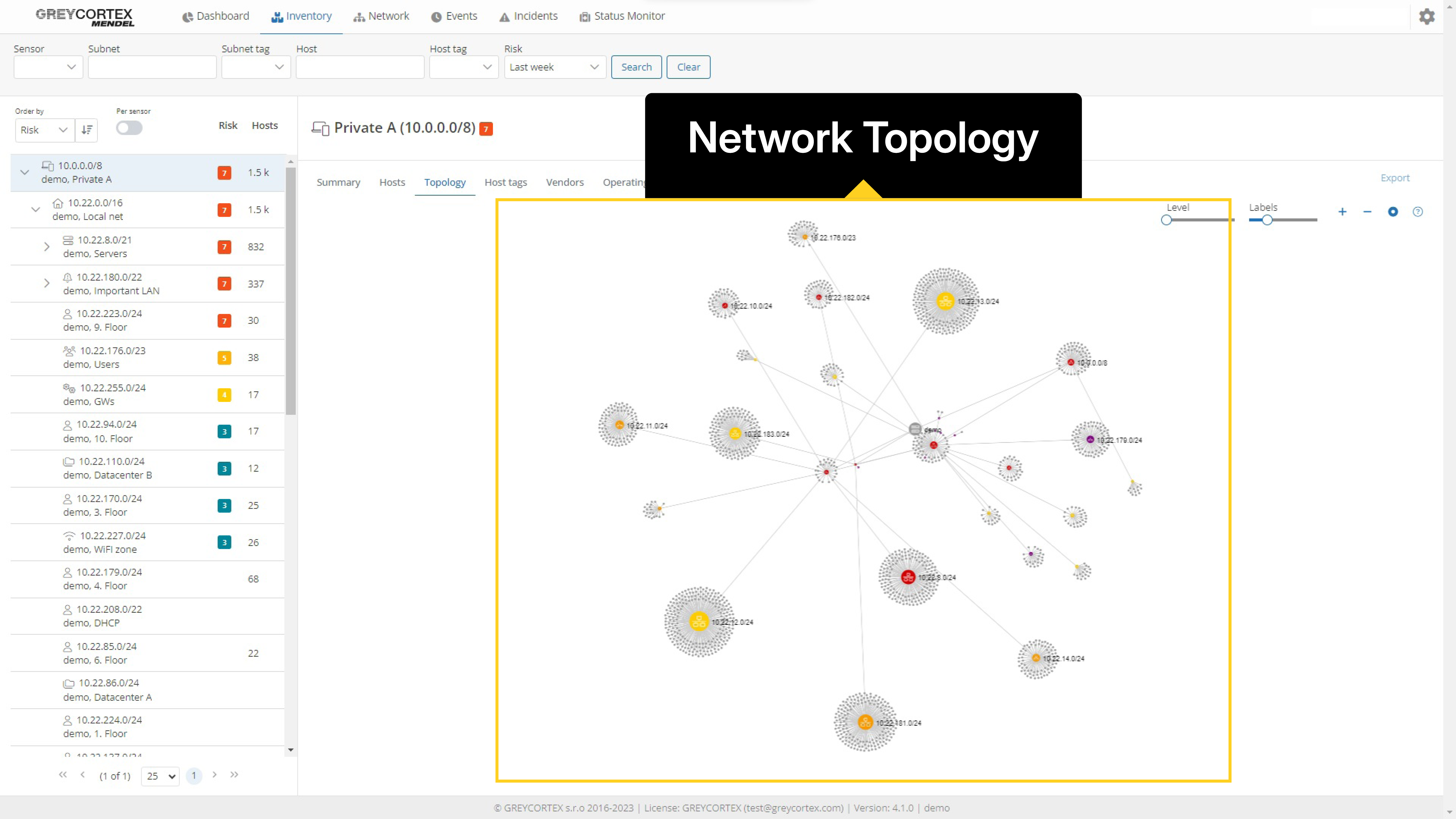
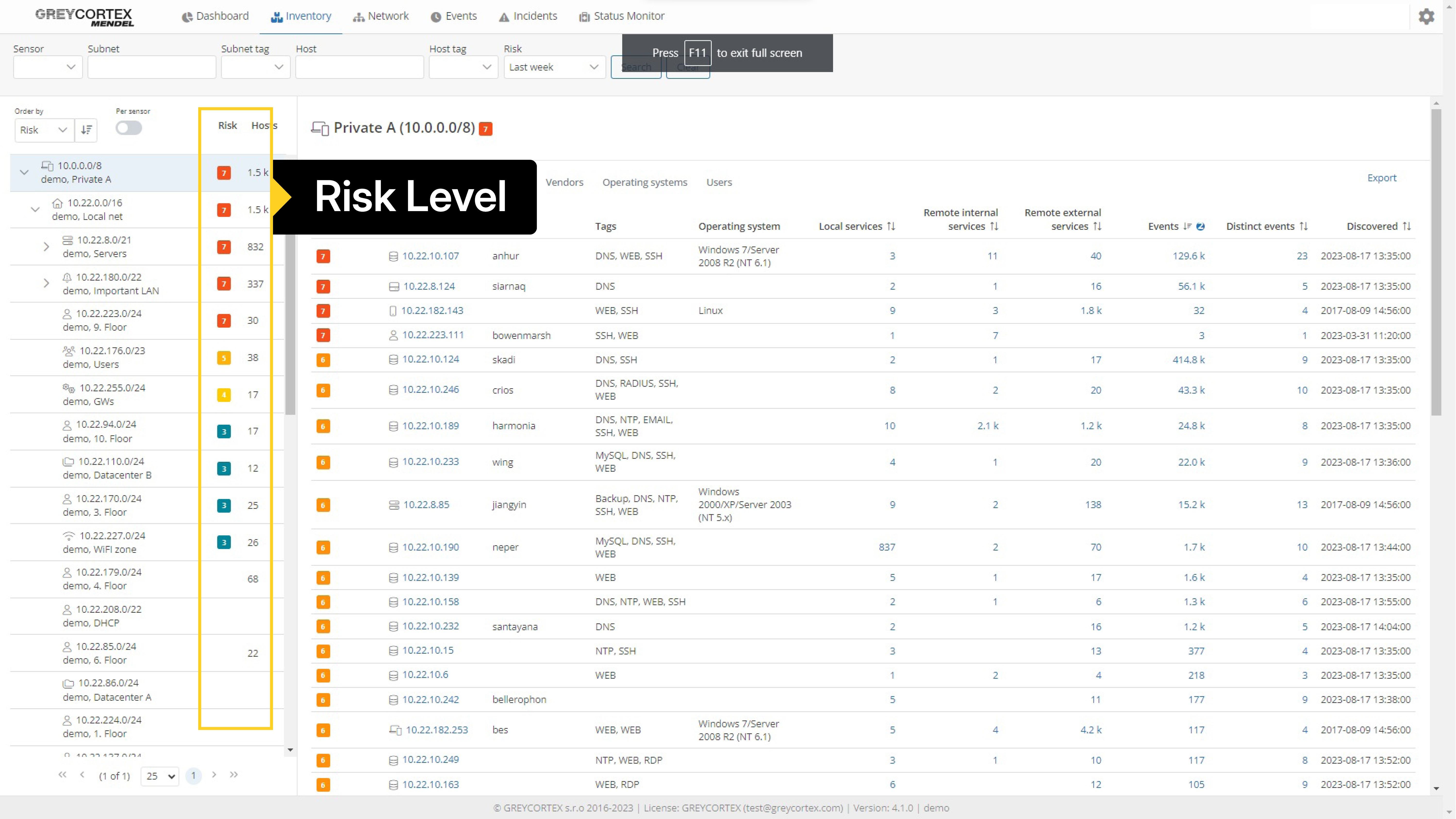
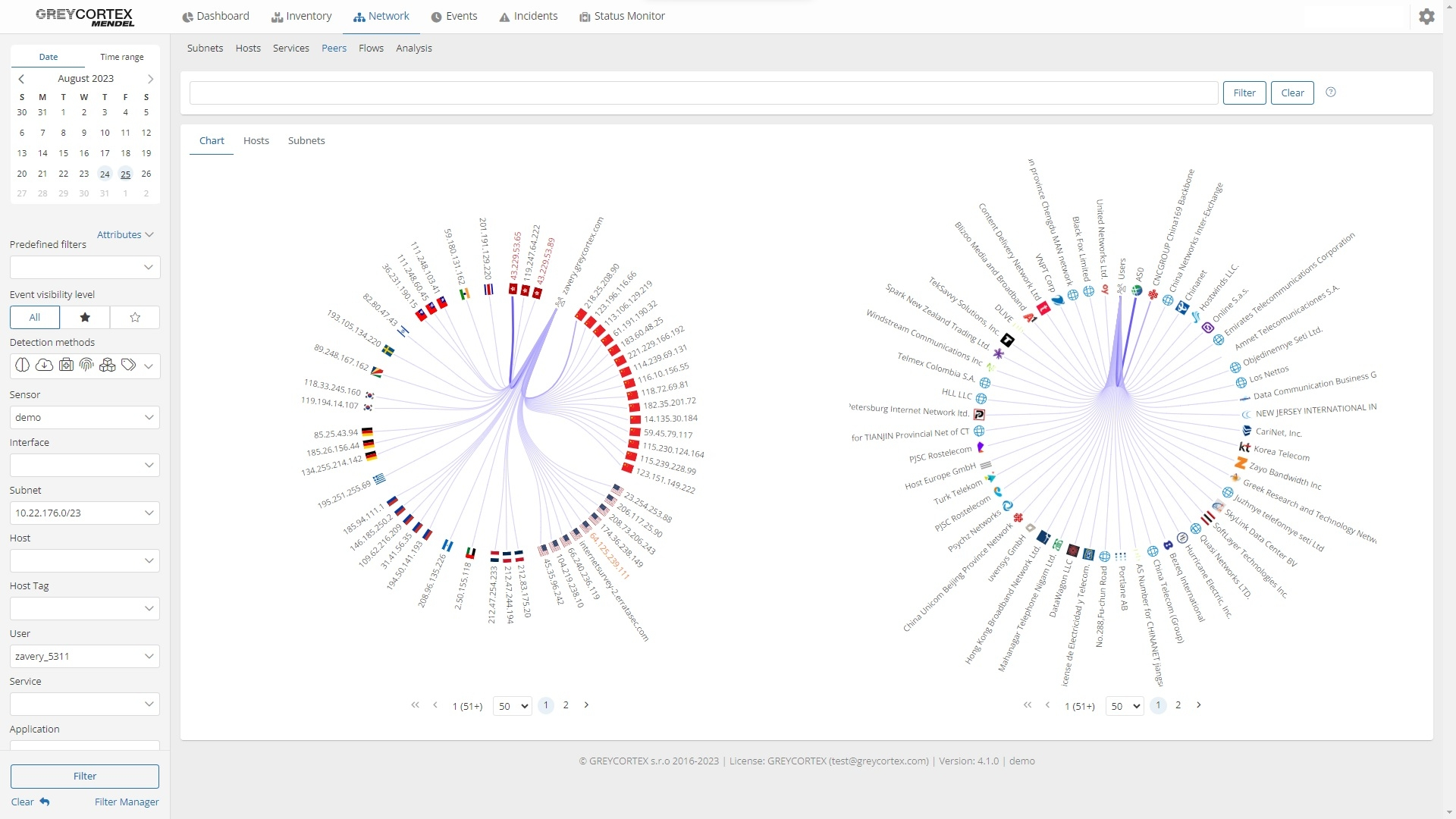
Mendel detects and stores information about every device communicating on your network. Use it to view a list of networks and subnets and see in detail the devices in these subnets. This overview is supplemented with information about the risk level of these devices and subnets, and detailed information about hostname, tags, operating system, and other parameters.
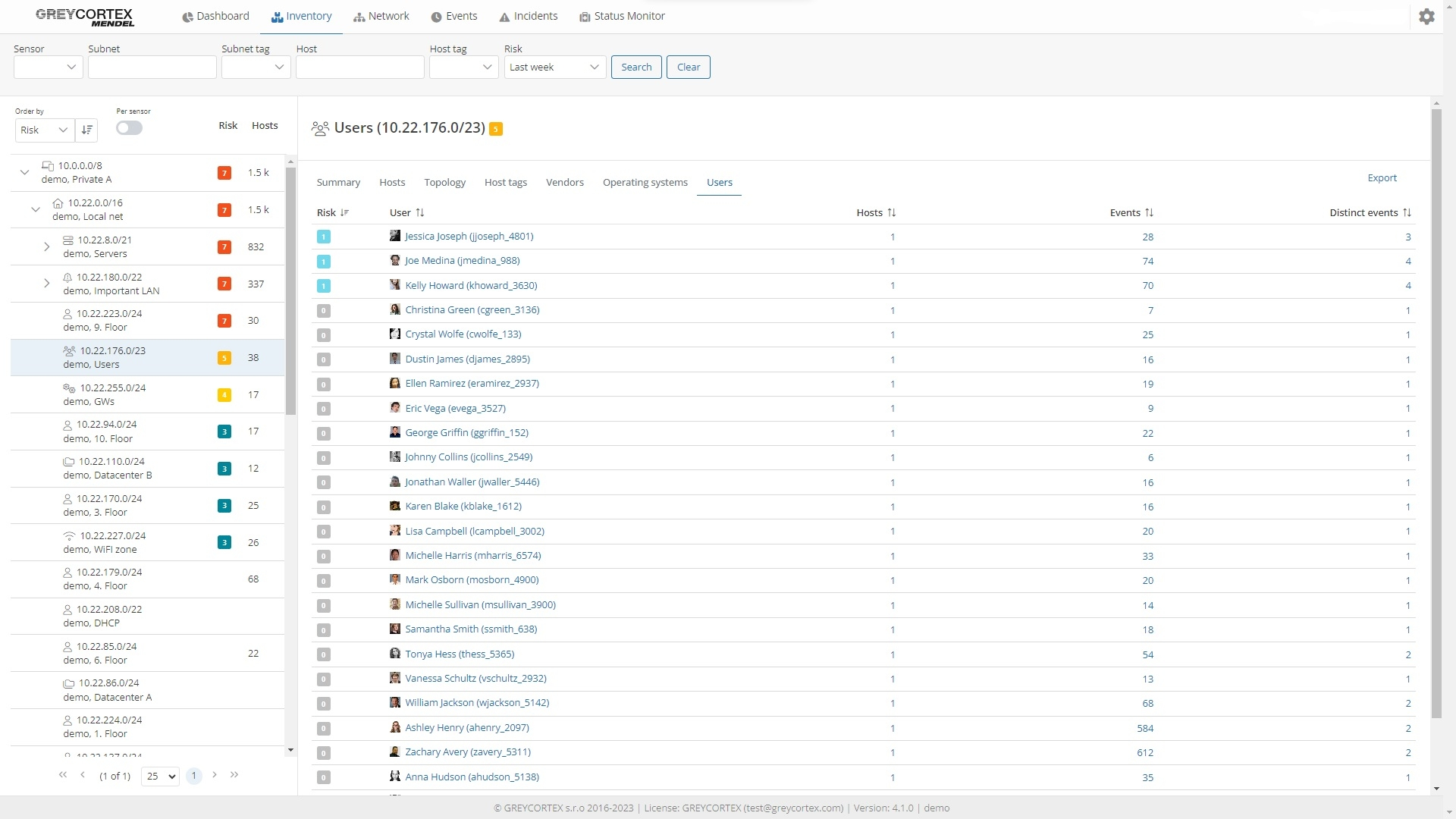
In the system, you will see a visualization of the individual connections between devices and networks as well as an overview of users. By integrating this with identity sources such as Active Directory or an LDAP server, Mendel connects specific communications to individual users.
Risk management
Understanding which systems are critical—and the impact of their failure—is fundamental. Mendel allows organizations to identify and prioritize key assets, enabling them to assess the potential consequences of disruptions.
By identifying the criticality of assets, organizations can allocate resources effectively, focusing on what truly matters to their operations and compliance efforts.
For instance, a manufacturing company used Mendel to uncover inadequate segmentation around a legacy control system. Addressing this gap protected them from a ransomware attack that could have halted production.
Mendel allows you to filter the communication clients that access a particular service or application as a basis for determining the criticality of those services and applications.
Human resource security and access control
Monitoring user behavior and access is vital to preventing unauthorized activity. Such examples are users communicating with a system to which they should not have permission to communicate, accessing a VPN with an account or remote access that should be blocked, or an external vendor having access to a company’s internal network that occurs after a contract has been terminated.
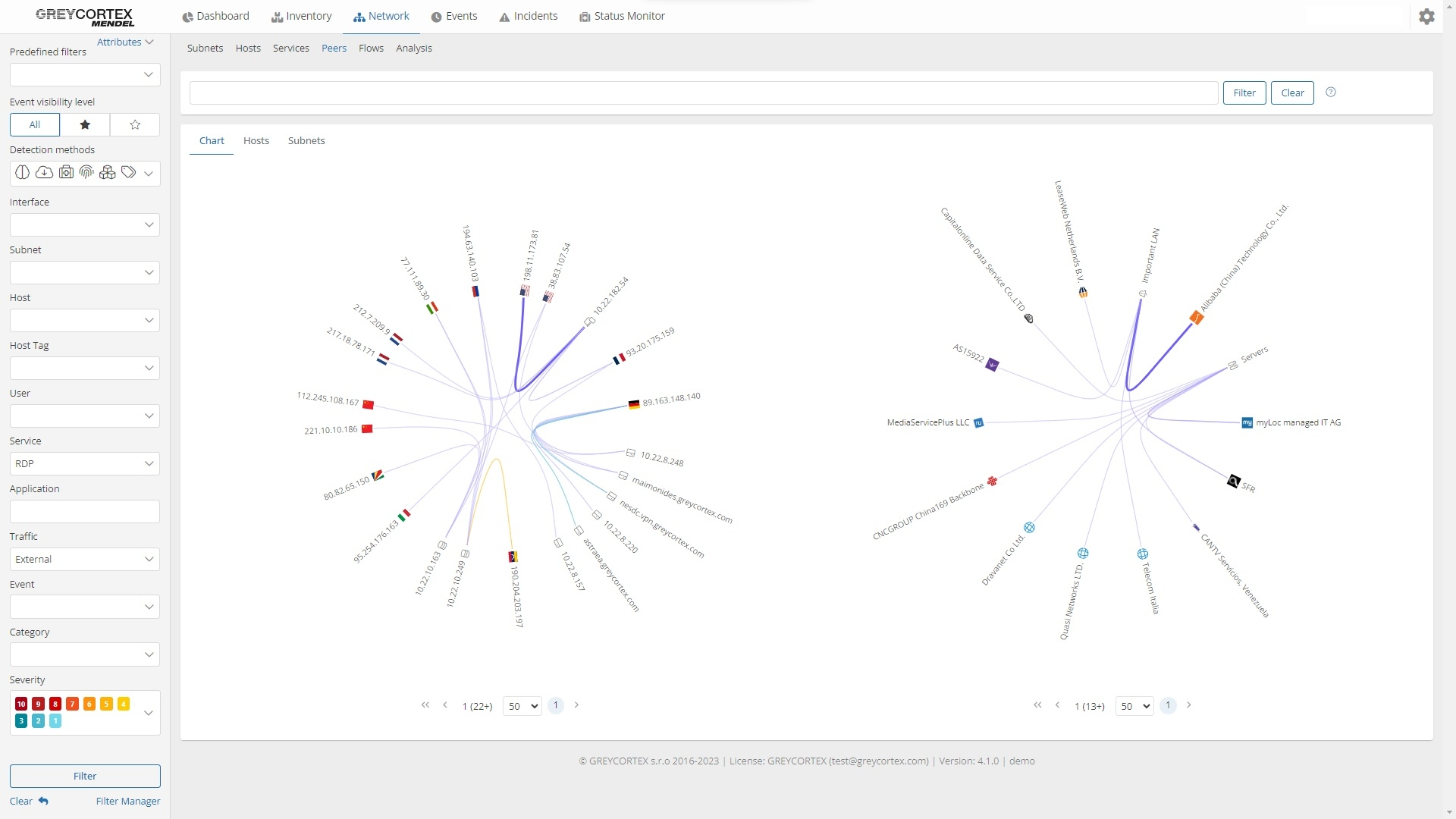
Mendel identifies unusual access patterns, such as attempts to log into restricted systems or use compromised credentials.
Our customer discovered that an employee’s credentials were being misused to access sensitive applications after hours. Mendel flagged the anomaly, enabling the IT team to act swiftly and prevent a breach.
By integrating Mendel with asset management tools or identity sources, it is possible to create a list of users and explore their communication with other users and services. This allows you to check whether there is a user on the network who should not be there.
Cybersecurity audit
Regular audits ensure that security measures align with daily operations. While traditional audits are conducted, for example, twice a year, Mendel enables you to carry out continuous verification of policies and compliance on a daily basis.
Security of communication networks
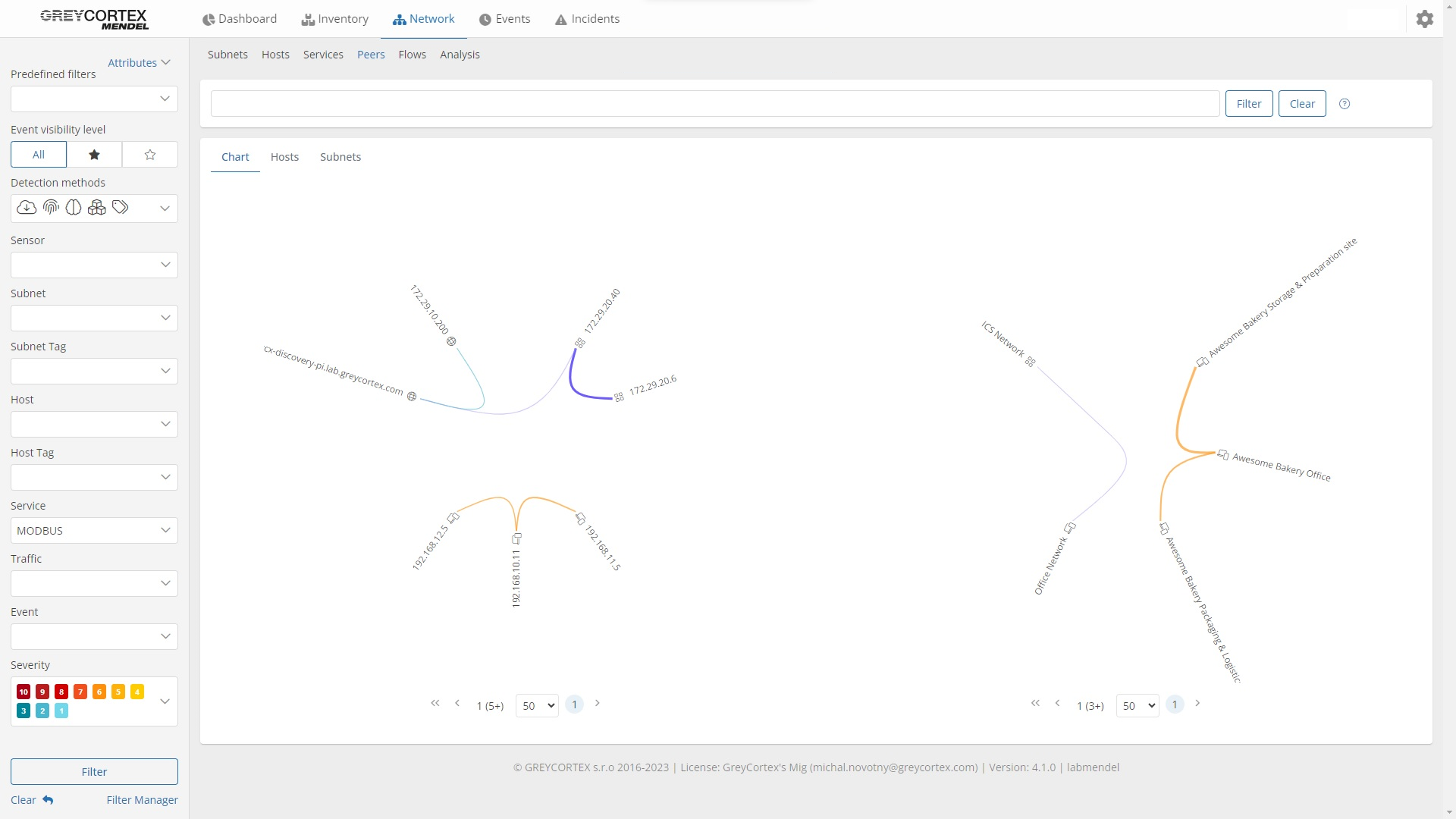
Network segmentation is a cornerstone of effective cybersecurity. With GREYCORTEX Mendel, you can easily verify the correct implementation of your network segmentation. Mendel provides clear insights into whether devices from one subnet are improperly communicating with devices in another subnet or are accessible from the Internet when they shouldn’t be.
Consider critical production devices, these are typically restricted to an internal network for security reasons but may occasionally require temporary Internet access for upgrades or remote servicing. If this access is not revoked after use, Mendel will detect and alert you to any unauthorized communication, ensuring your network remains secure.
Mendel’s capabilities go further, processing protocols like MODBUS and other OT-specific protocols to visualize communication flows for production devices. This helps verify not only where these devices are communicating but also whether the communication complies with security policies.
Additionally, Mendel simplifies the detection of illegitimate connections. For example, you can filter and monitor Remote Desktop Protocol (RDP) communications that might be restricted by company policy or identify unauthorized TeamViewer connections.
Detection of cybersecurity events
Detection is one of the key capabilities of GREYCORTEX Mendel, along with its recording and analysis. All this is key for effective incident prevention.
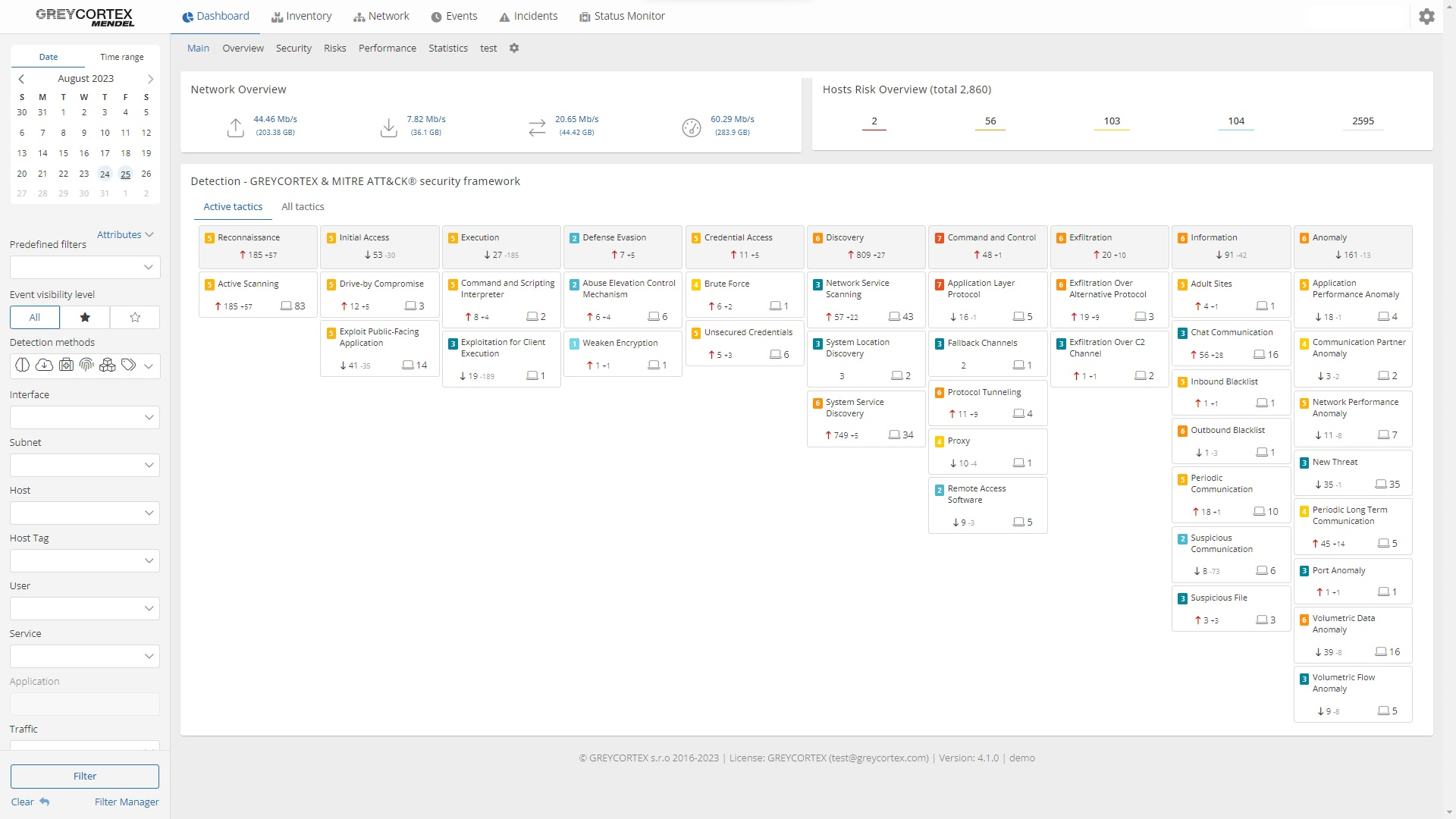
Mendel excels at identifying threats by analyzing network traffic and detecting both signature-based and anomalous behavior. This capability allows organizations to address issues at different stages of a cyberattack.
For example, Mendel detects command-and-control communication, a hallmark of advanced persistent threats, and brute force attacks, which are a common tactic in ransomware campaigns. Also, it detects other dangerous behaviour, such as scans or tunnels.
Event logging
One of NIS2’s key requirements is retaining cybersecurity event records for at least 18 months. GREYCORTEX Mendel lets you simplify compliance by securely recording all mandatory data and making it easily traceable over months or even years—limited only by your available storage capacity.
Mendel also supports seamless integration with other tools through its ability to upload and export PCAP files. This feature enables you to analyze records externally or import PCAPs back into Mendel for detailed investigations, ensuring your organization stays agile in handling cybersecurity events.
Analysis of cybersecurity events
Continuous and centralized evaluation of detected cybersecurity events is essential for maintaining a robust security posture. This process involves identifying correlations, assessing the relevance of sources, and generating alerts—whether automatically in real-time or through manual configuration.
With GREYCORTEX Mendel, you gain the ability to drill down into the specifics of every detected event. Mendel categorizes events using the MITRE ATT&CK Framework, providing a structured and industry-recognized approach to understanding threats. Additionally, it offers various intuitive views and filters, enabling you to analyze your data from multiple perspectives and focus on what matters most to your organization.
Cryptographic algorithms
GREYCORTEX Mendel helps you verify that your systems are using up-to-date encryption standards and eliminates the risks associated with unencrypted communications or plaintext password transmissions.
For example, Mendel flagged several plaintext password transmissions in a client’s system, enabling them to enforce encryption policies and prevent credential theft.
Additionally, Mendel checks the validity of communication certificates, ensuring that your encrypted connections are both secure and compliant with best practices.
Security of industrial assets
The NIS2 Directive places significant emphasis on securing industrial networks, an area where many organizations still face challenges. GREYCORTEX Mendel addresses these gaps by supporting industrial protocols like MODBUS, OMRON, BACnet, and others, enabling comprehensive monitoring of operational technology (OT) environments.
Beyond analyzing IT network traffic, Mendel visualizes communication between devices up to level 2 of the Purdue model, including sensors, motors, and other industrial components. With proper configuration, it can extract detailed insights about OT devices, such as furnace temperatures, centrifuge speeds, pipeline pressures, and water levels in storage vessels.
Mendel delivers critical data to ensure the reliability and security of production infrastructure, including:
- Identification of Common Vulnerabilities and Exposures (CVEs) affecting OT devices
- Configuration settings of industrial systems
- Firmware information for better version control and security assessments
Prepare in Time
Applicability, enforcement, and fines will vary from one EU Member State to another. Yet in cybersecurity, more than anywhere else, the saying “yesterday was too late” applies.
There is no need to panic, but don’t underestimate the security of your business or institution. Your organization doesn’t need to face NIS2 alone. Whether you’re just starting your compliance journey or refining existing processes, GREYCORTEX Mendel provides the visibility and control you need to succeed.
Schedule a demo today and let us show you how we’ve helped organizations like yours achieve peace of mind.
Categories
- Company News (34)
- Product News (26)
- IT/OT Security (37)
- Webinars (5)