With segmentation and core services covered, the focus now shifts to enforcing policies on usage, user behavior, and encryption to maintain visibility and ensure compliance across all layers of your network. These controls are critical for mitigating internal risks and upholding your secure communication standards.
GREYCORTEX Mendel supports this effort by providing you with clear insights, alerting you about violations, and helping your teams validate whether your policies are being followed in practice.
Missed the beginning?
🔗 Read Part 1 to explore how Mendel helps you enforce segmentation and control your core network services.
User Access Policies and Behavioral Violations
Even trusted users and systems can introduce risk if policies are not clearly enforced. Monitoring what is allowed and what is not helps you uncover subtle violations that could otherwise go unnoticed.
Policy violation: Forbidden protocols or apps (RDP, TeamViewer, Dropbox, etc.)
Relevant for NIS2
Some organizations prohibit remote-access tools or file-sharing apps to reduce risk and maintain control over their IT environments. When unauthorized protocols are used, they may introduce new attack vectors or enable remote exploitation.
Validation with Mendel
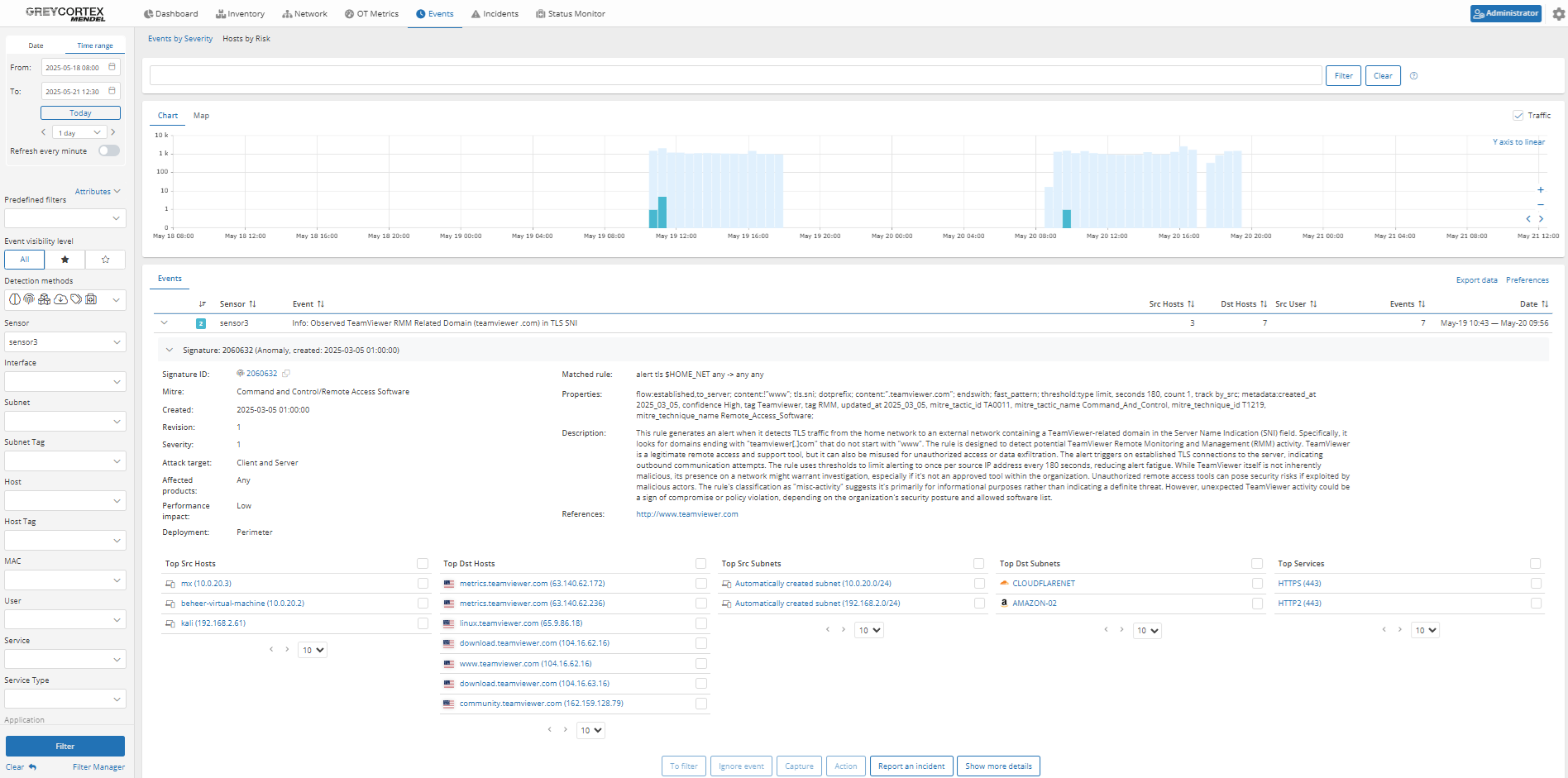
Mendel directly detects the use of unauthorized applications. Your analysts can filter for specific protocols to confirm whether a session occurred and if it was successful, including details about session duration, data transfer volumes, and communication content. This helps you verify whether users violated your internal policies, and allows you to add legitimate usage to an exception list to avoid future alerts.
In our case, Mendel has identified and flagged multiple devices that have downloaded and used TeamViewer. Analysts can then investigate whether these hosts were authorized and, if appropriate, whitelist the IPs to prevent future alerts.
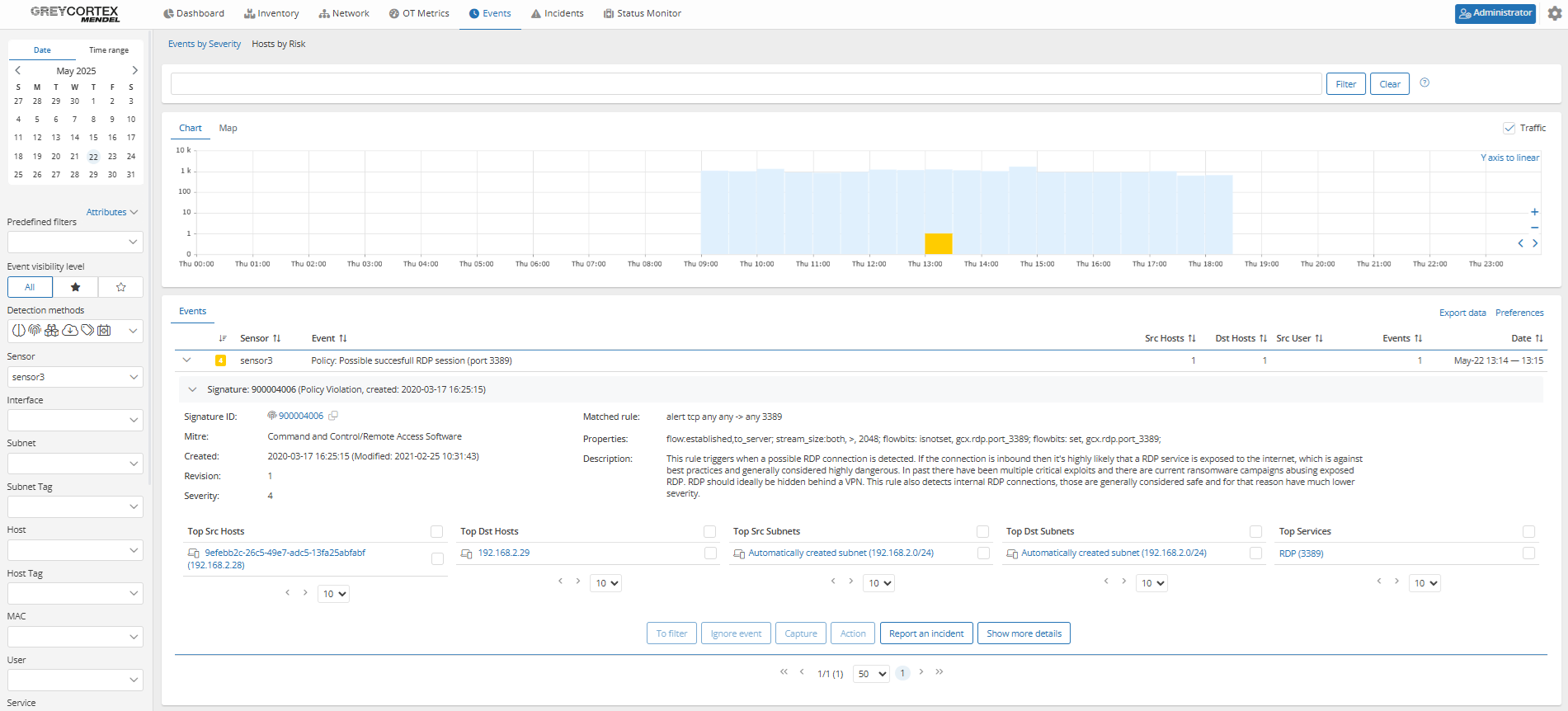
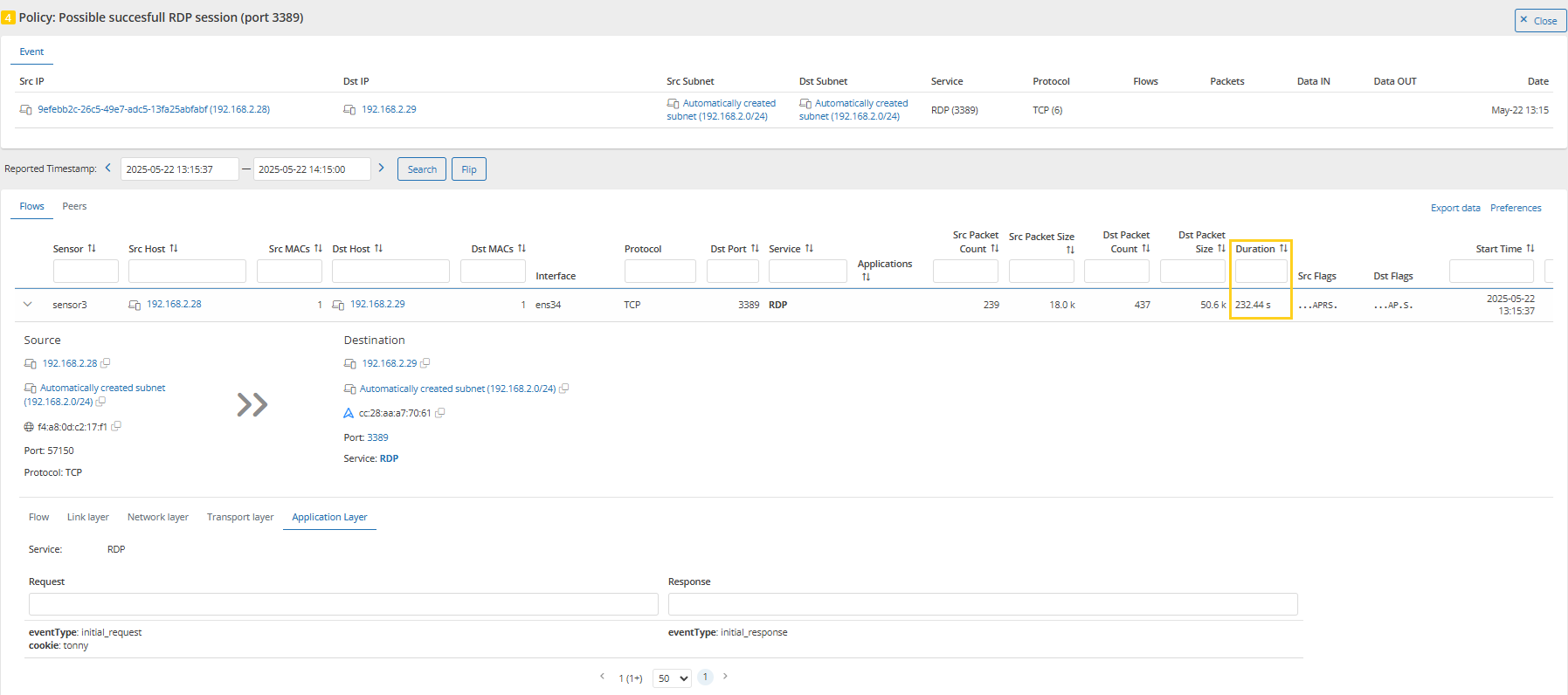
In another example, Mendel has captured a potential RDP (Remote Desktop Protocol) session. By drilling down into the event, analysts can identify the user involved and review the session duration.
Policy violation: Communication to forbidden destinations or services
Relevant for NIS2
Certain destinations, such as foreign countries, blacklisted IPs, or unauthorized services, are often restricted to reduce risks. Detecting such traffic reveals overlooked exceptions or malicious tools trying to evade controls.
Validation with Mendel
Mendel detects and alerts you about communication with blacklisted IPs. Your analysts can use predefined or custom filters to review connections by source and destination IPs, traffic volume, and packet counts. The Network Analysis tab provides you with extensive filtering and search options, enabling your teams to conduct deep investigations across the entire network.
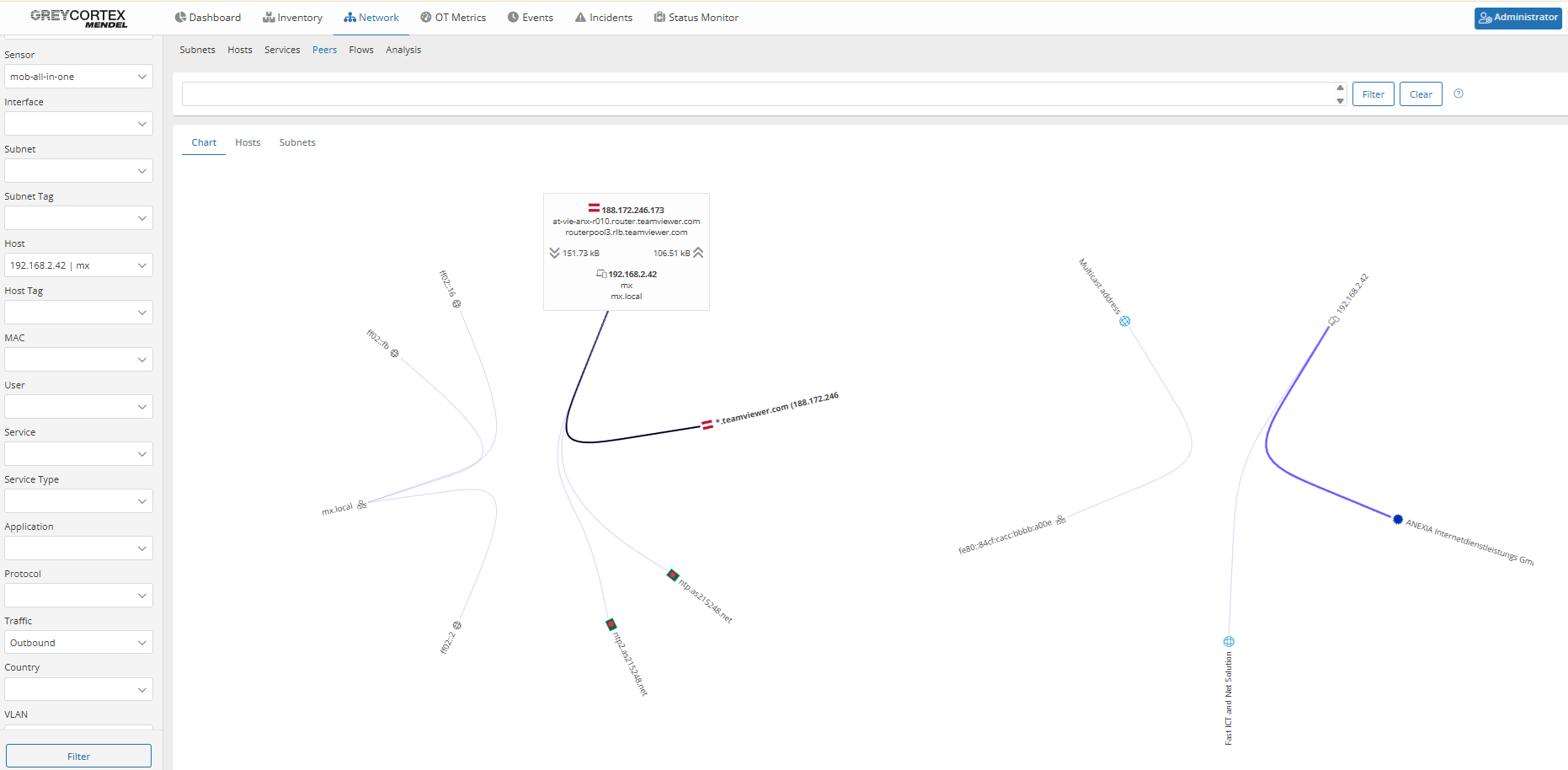
As an example, Mendel detected a TeamViewer DNS request originating from host mx (192.168.2.42). By drilling down, analysts confirmed that a connection was successfully established, indicating a potential policy violation or unauthorized remote access.
Mendel allows your analysts to identify which user is behind suspicious traffic. This helps you verify whether access to forbidden destinations or tools was legitimate or a policy violation.
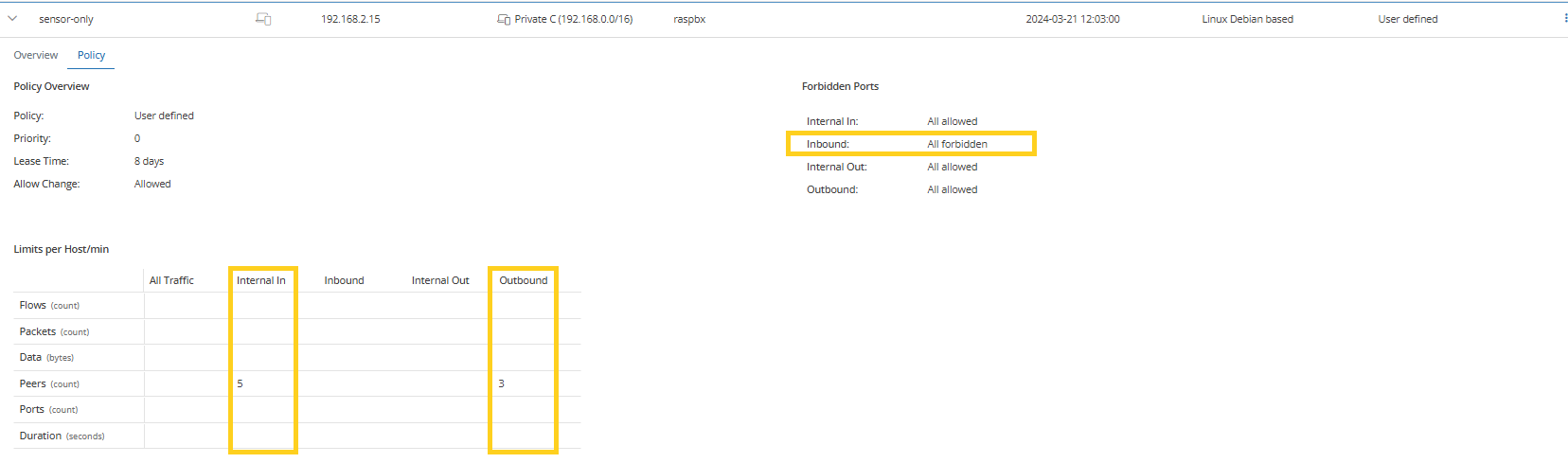
Policy violation: Excessive peer communication
Certain devices, like controllers in manufacturing or internal phone servers (PBXs), are expected to communicate with a limited set of peers. New or unusual connections may signal misconfiguration or unauthorized activity.
Validation with Mendel
Mendel enables your analysts to define peer count limits for individual hosts or entire subnets, helping you to enforce expected communication boundaries.
For example, if a PBX server communicates with more peers than its known SIP trunks and internal phones while inbound Internet traffic is restricted, Mendel will flag it for review.
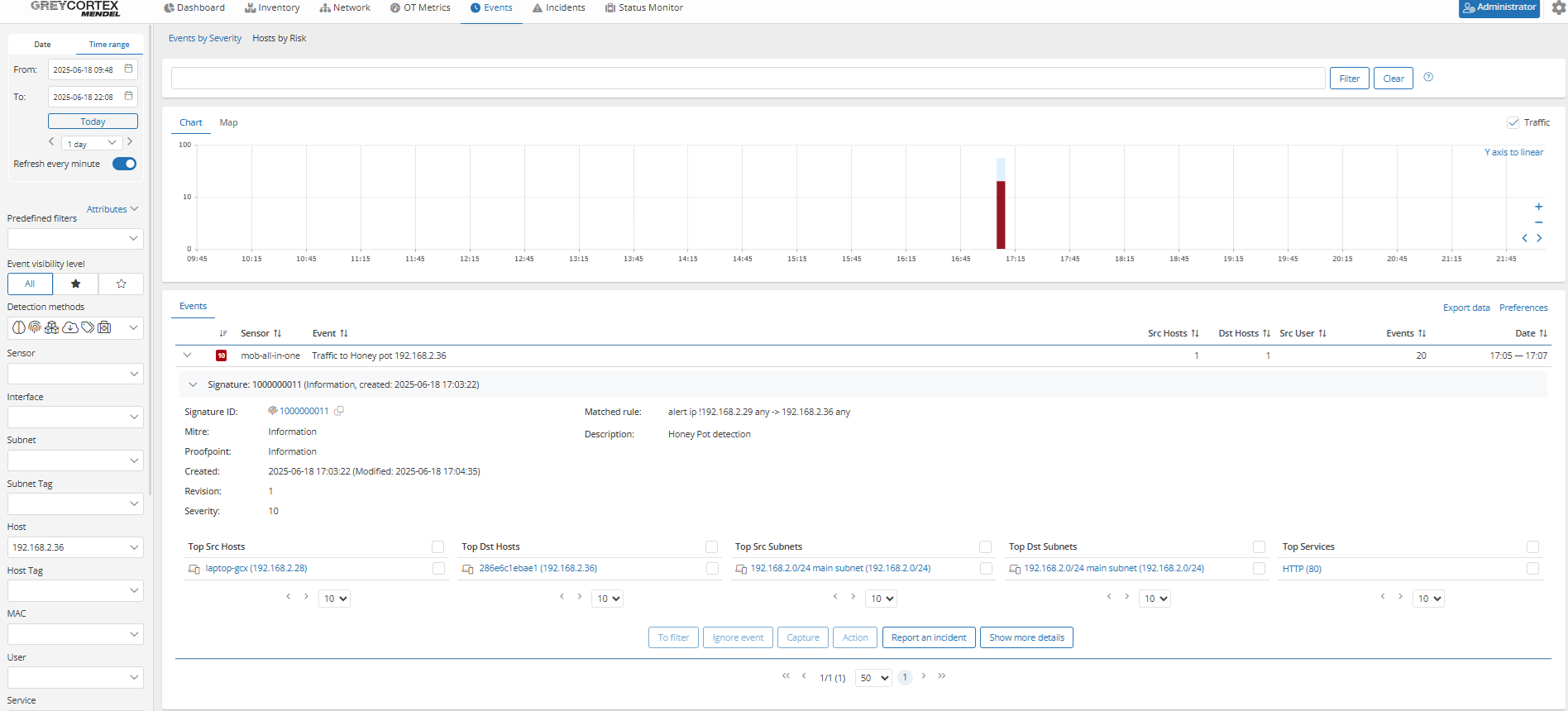
Policy violation: Unauthorized communication with honeypots
Honeypots are intentionally exposed systems used to detect suspicious activity inside the network. Typically, only predefined systems such as admin tools or security scanners should communicate with them. Any other connection attempt may indicate lateral movement or internal scanning.
Validation with Mendel
Mendel allows your teams to define which systems are authorized to communicate with honeypots and alerts your analysts to any unauthorized attempts.
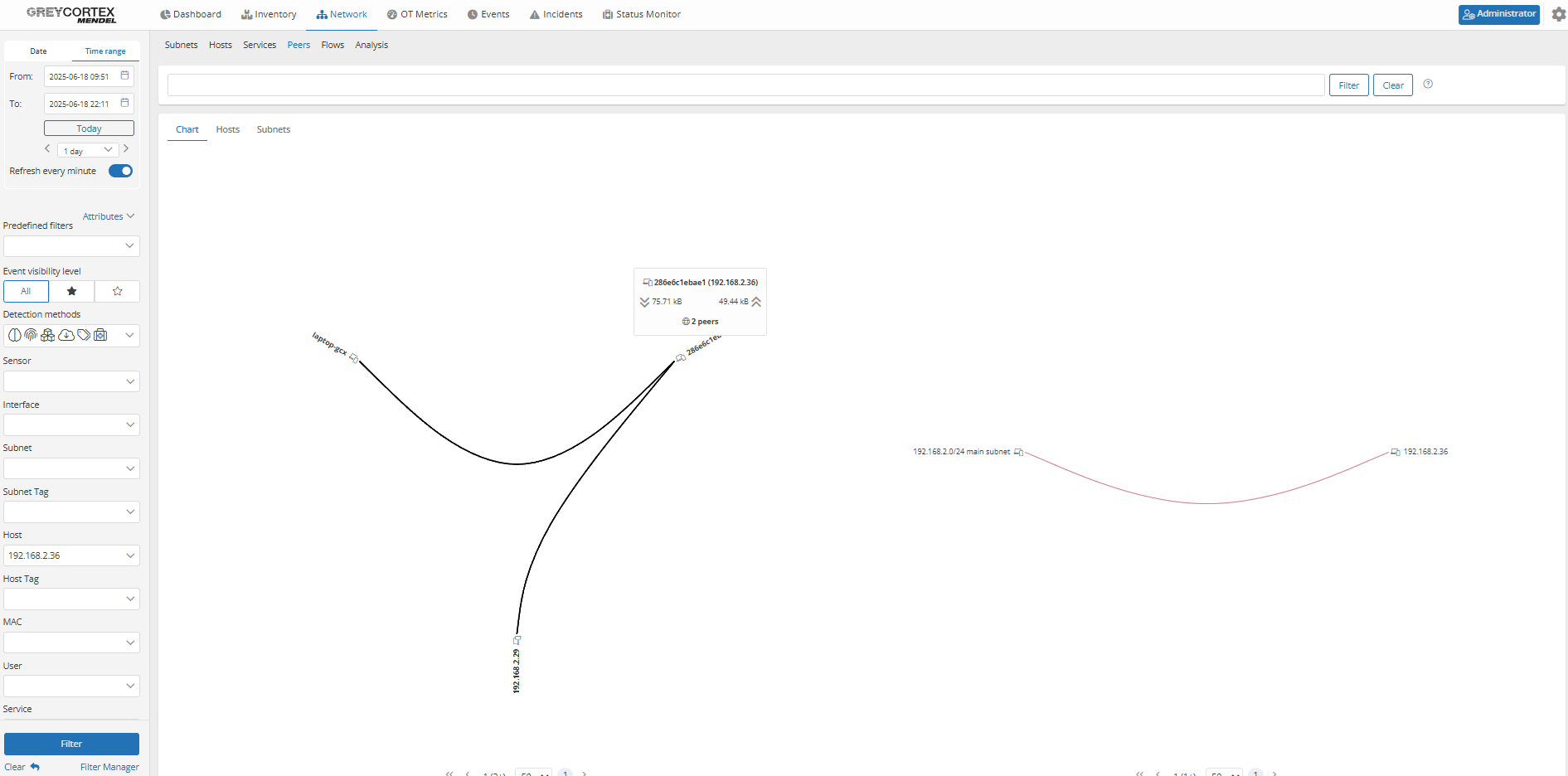
In the example below, only the management PC is allowed to communicate with the honeypot at 192.168.2.36. When another device (192.168.2.28) initiates a connection, Mendel triggers an alert.
The peer graph confirms and visualizes that the honeypot was accessed by both permitted and unauthorized devices.
Encryption Standards and TLS Usage
Cryptographic standards are a foundational layer of secure communication. Monitoring certificate validity and protocol versions helps you identify weak encryption before it becomes a vulnerability.
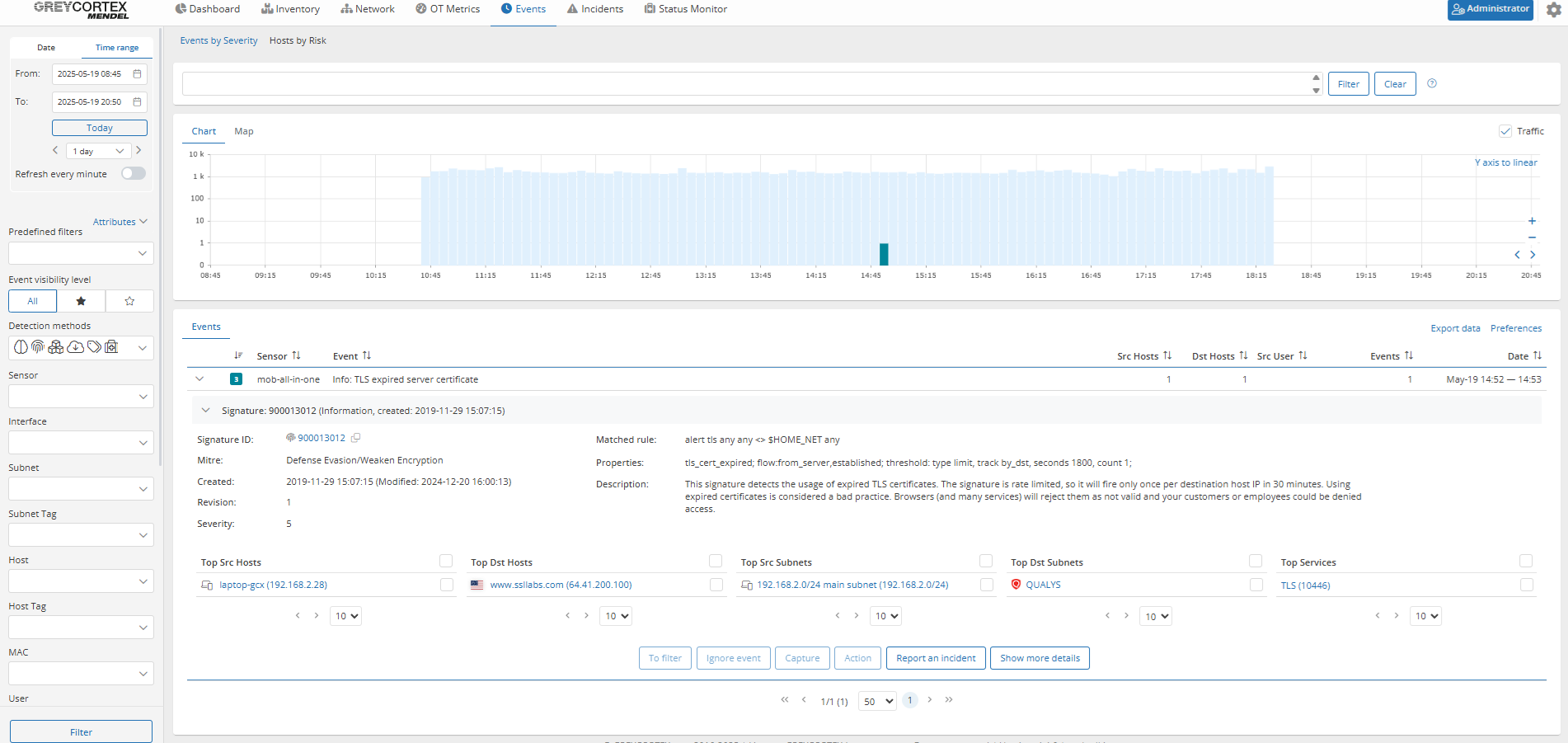
Policy violation: Expired TLS certificates in use
Relevant for NIS2
TLS certificates are a critical part of trusted communication. If a certificate has expired, systems may reject the connection, users may be exposed to spoofed services, or sensitive data may be transmitted without adequate encryption.
Validation with Mendel
Mendel alerts you when expired certificates are detected or when a certificate is approaching its expiration date.
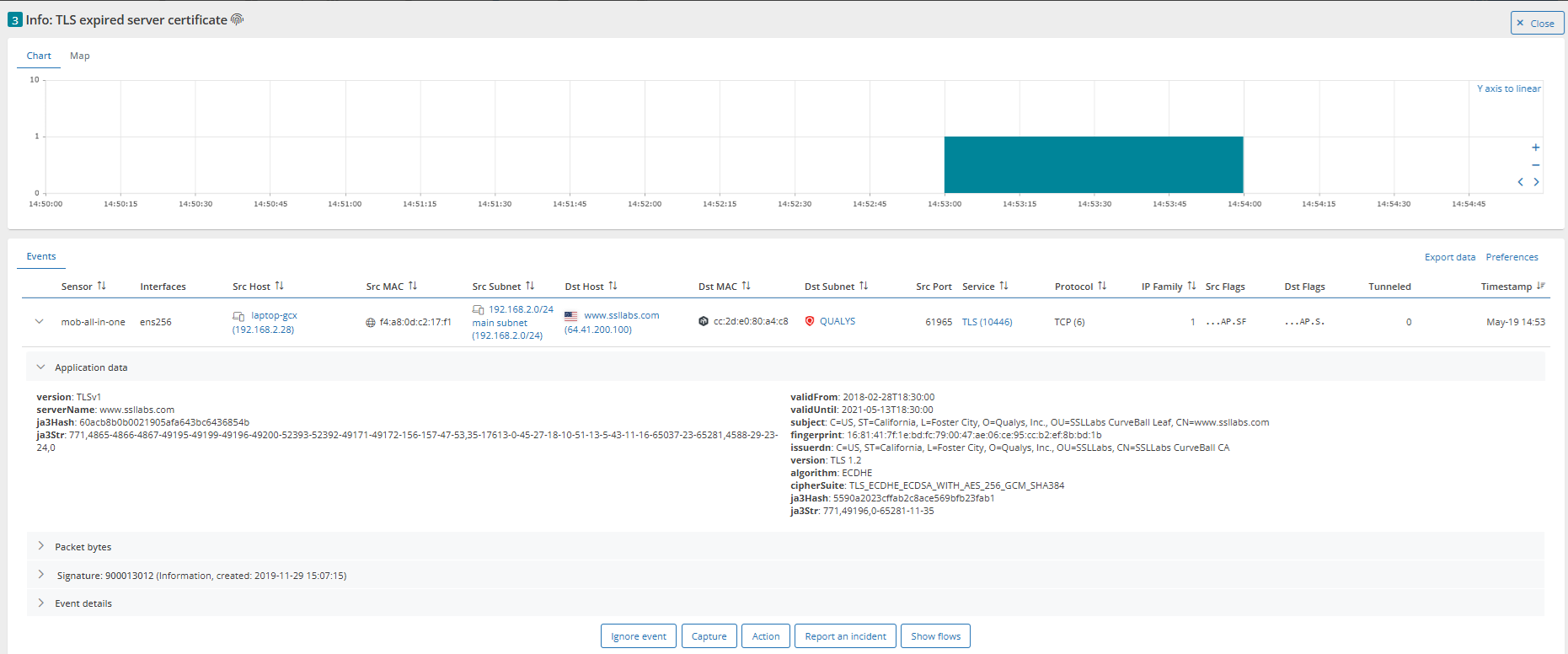
For example, Mendel has found one internal system using a certificate that expired in May 2021.
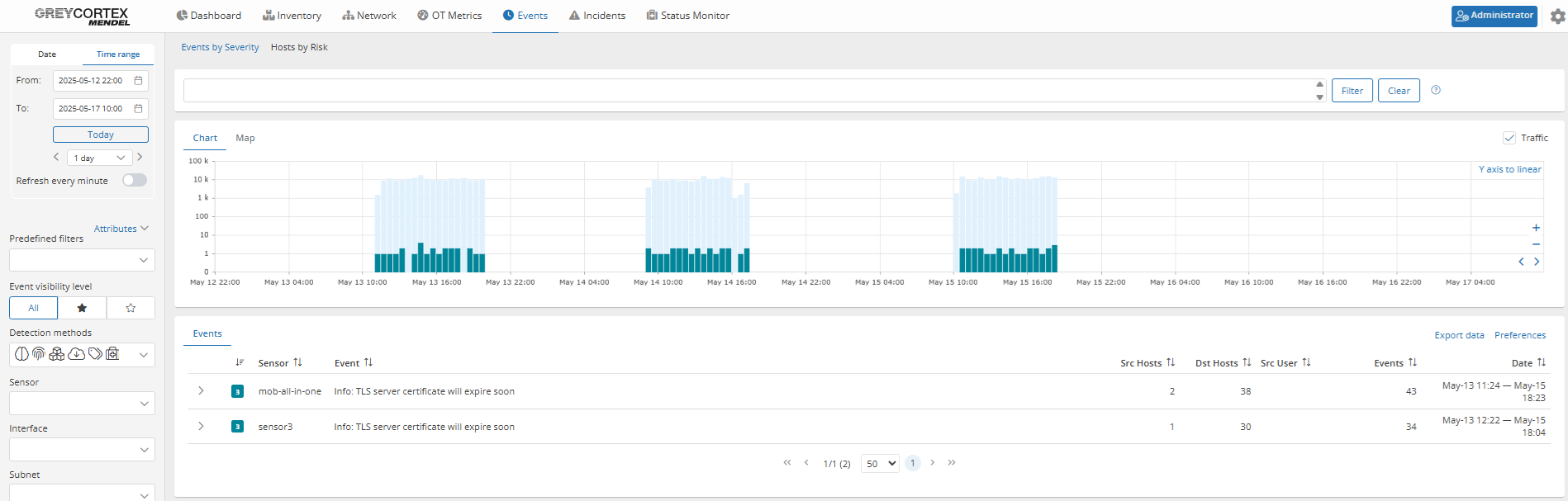
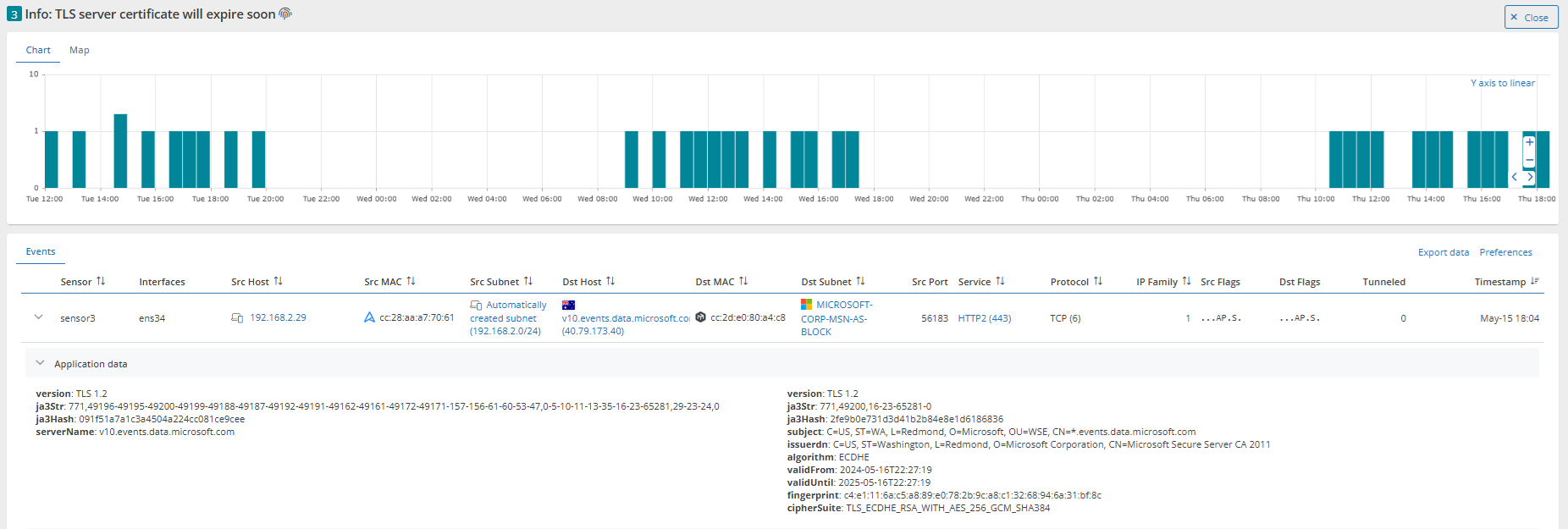
In another case, Mendel has flagged an upcoming expiration several days in advance, giving administrators time to respond before any disruption occurs.
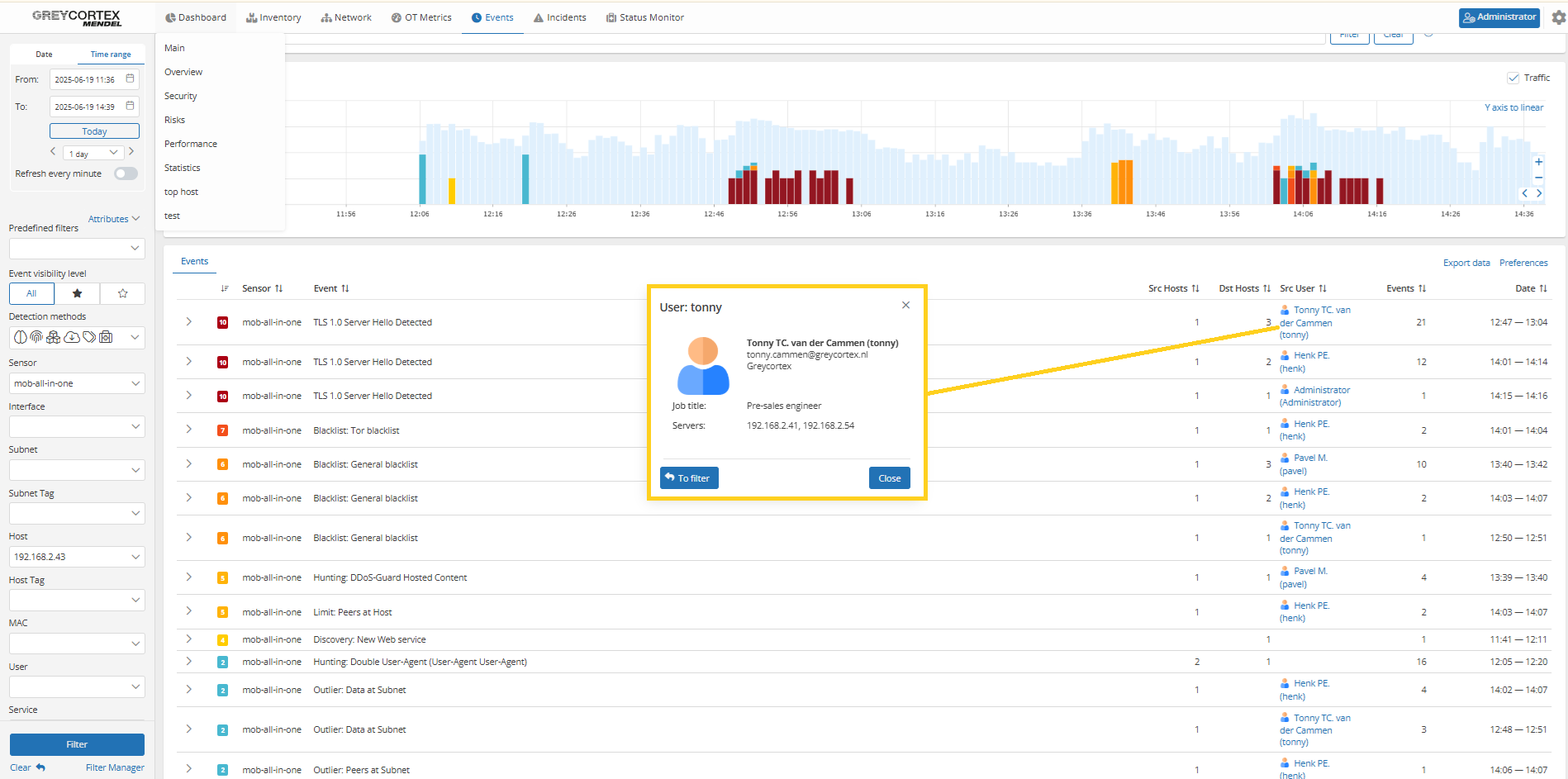
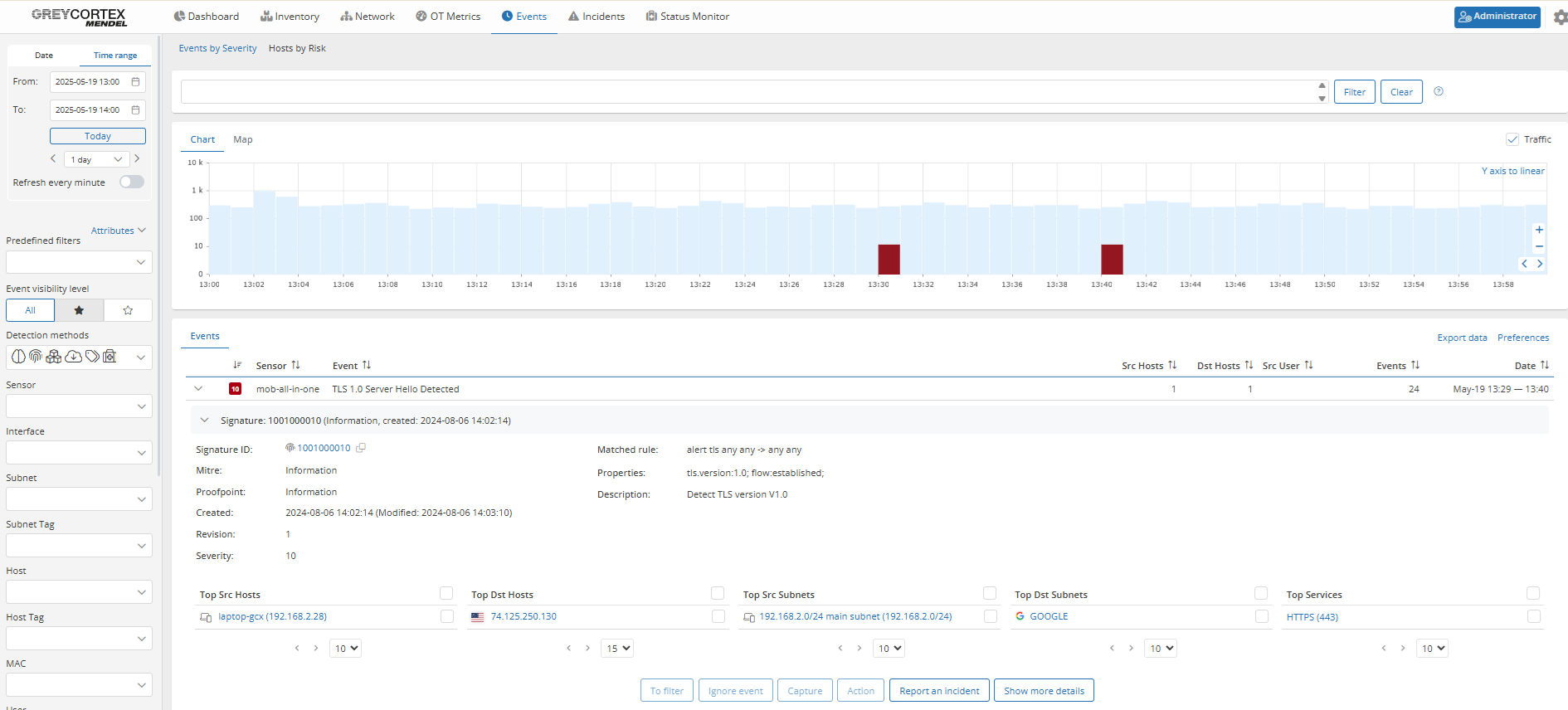
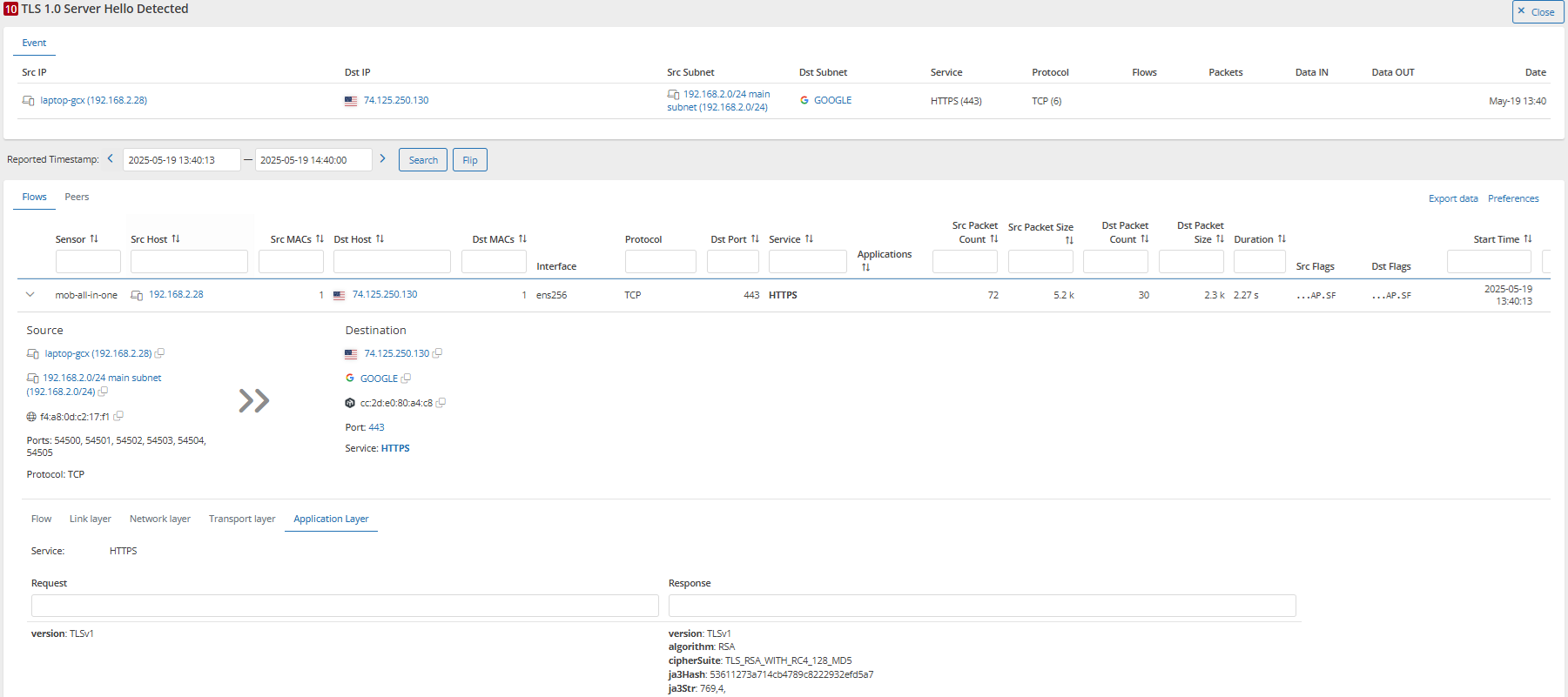
Policy violation: Outdated TLS versions and cipher suites
Relevant for NIS2
Obsolete TLS versions and weak cipher suites expose your encrypted traffic to known vulnerabilities. Regulatory frameworks like NIS2 urge organizations like yours to stop using TLS versions below 1.2 to reduce attack surfaces and ensure strong encryption standards.
Validation with Mendel
Mendel allows you to configure alerts when outdated TLS versions are used. To ensure secure communication, it is recommended to use TLS 1.2 or 1.3. Achieving this typically involves updating the operating system, browser, or other client software.
For example, an event has shown that one device was still communicating using TLSv1.0.
Strong Policies Require Strong Evidence
Security policies do more than reduce risk. They help you demonstrate accountability to regulators, customers, and internal stakeholders alike. As expectations rise under frameworks like NIS2, proving that internal rules are applied consistently becomes a core part of modern cybersecurity governance. It is no longer enough to assume policies are being followed. You need clarity and verifiable evidence.
Mendel helps organizations like yours move from assumption to evidence. It continuously validates how policies are enforced across the network, from encryption to identity controls, giving your team the visibility to act with clarity and confidence.
Need a second opinion on your enforcement? Request a security audit with Mendel.
Categories
- Company News (34)
- Product News (26)
- IT/OT Security (37)
- Webinars (5)